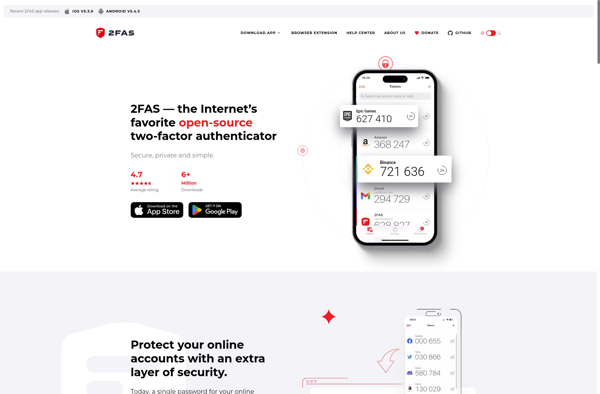
Description: 2FA Authenticator (2FAS) is a free, open-source two-factor authentication app for mobile devices. It enables users to easily set up two-factor authentication for added account security, with support for OTP, TOTP, and HOTP standards.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
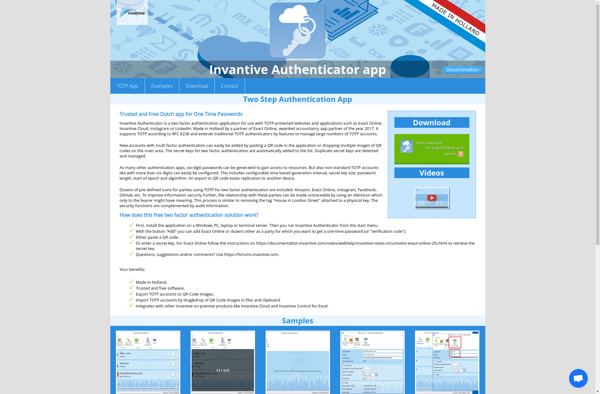
Description: Invantive Authenticator is a multi-factor authentication solution that provides additional security for accessing business applications and data. It uses push notifications, one-time passcodes, biometrics, security keys and other methods to verify user identity.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API