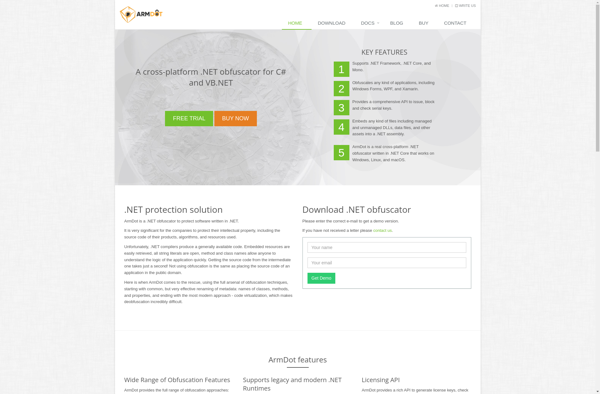
Description: ArmDot is an open-source software platform for developing and deploying machine learning models on edge devices. It enables running neural networks efficiently on resource-constrained hardware like microcontrollers and IoT devices.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
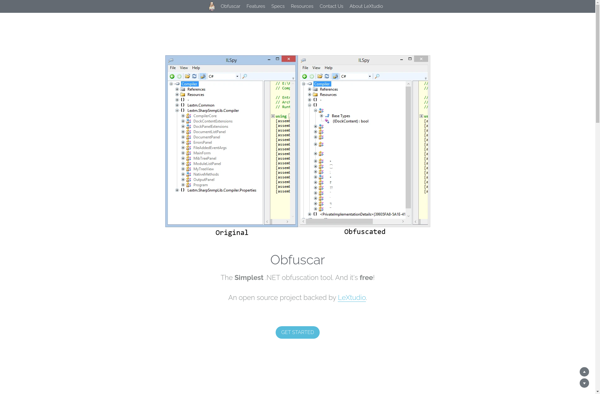
Description: Obfuscar is an open-source .NET obfuscator for protecting .NET assemblies against reverse-engineering. It works by obfuscating names, control flow, and data with features like renaming, control flow obfuscation, string encryption, and more.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API