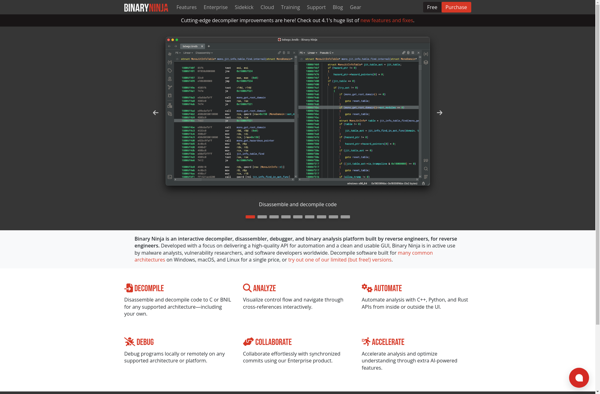
Description: Binary Ninja is a reverse engineering platform that allows security analysts to disassemble, analyze, and debug software. It supports a variety of architectures and file formats and provides a plugin architecture to extend functionality.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
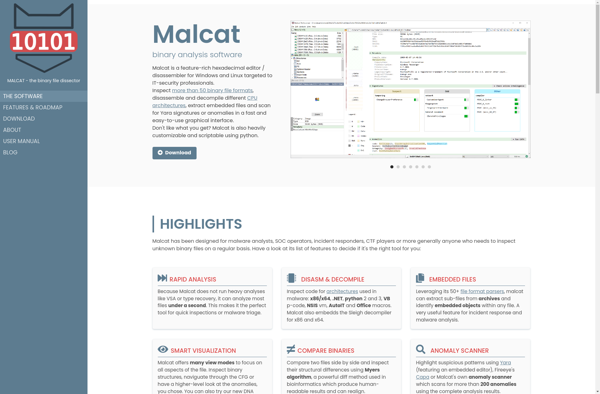
Description: Malcat is an open-source malware analysis tool that allows users to analyze malicious files, extract payloads, perform static analysis, and gather threat intelligence. It has support for a wide variety of file types including PE files, scripts, documents, and memory dumps.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API