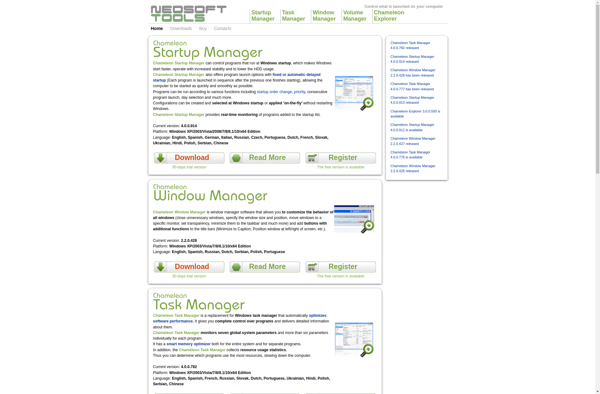
Description: Chameleon Shutdown is a free, open source software application for scheduling computer shutdowns, restarts, sleep, and hibernation. It allows users to easily automate power settings.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: Sentinella is an open-source SIEM (security information and event management) software that provides real-time analysis of security alerts and automated threat detection. It's designed to collect data from various systems and network sources to identify suspicious activity.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API