Description: CoinSwitch is a cryptocurrency exchange platform that allows users to compare rates across multiple exchanges and convert one cryptocurrency to another. It supports over 300 cryptocurrencies and has partnerships with major exchanges like Binance, OKEx, and KuCoin.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
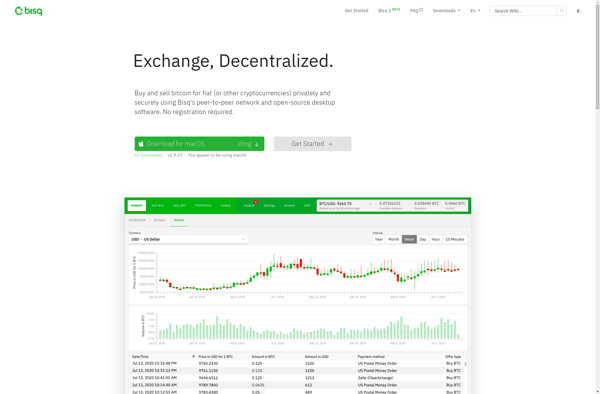
Description: Bisq is an open-source, peer-to-peer application that allows users to buy and sell cryptocurrencies in exchange for national currencies or alternative cryptocurrencies. It provides privacy and security by not requiring any personal information and using end-to-end encryption.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API