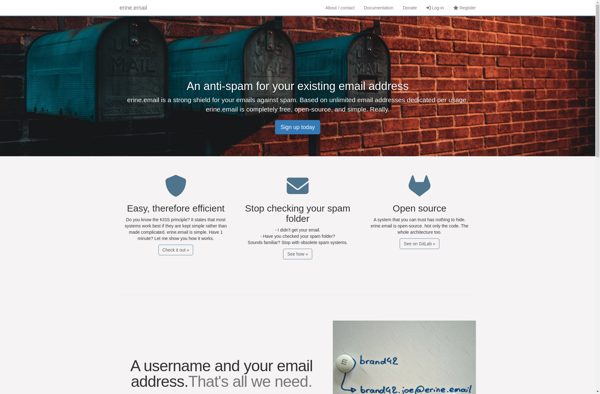
Description: Erine.email is an email software that focuses on privacy and security. It offers end-to-end encryption, anonymous email addresses, inboxcleaner to remove tracking pixels, and secure cloud storage. It aims to provide a private alternative to Gmail and other popular email services.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
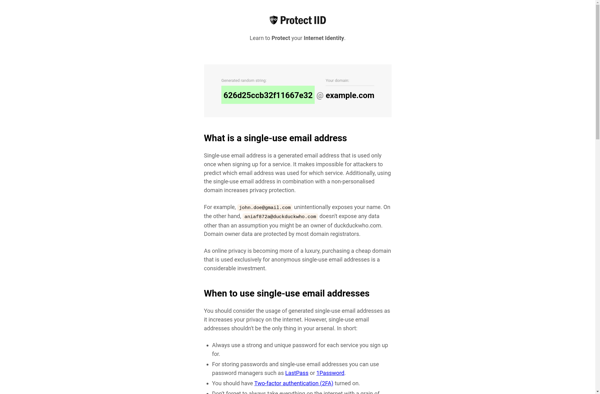
Description: Protect IID is a privacy software that helps prevent the leakage of personally identifiable information (PII) by masking or replacing sensitive data fields. It works by scanning databases, files, and applications to discover PII and then applying transforms to encrypt, tokenize, or redact that data.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API