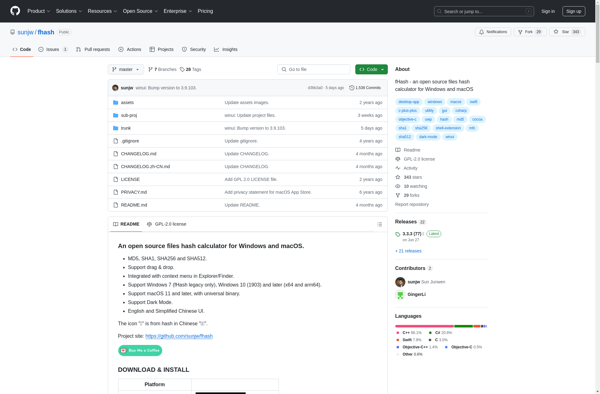
Description: fHash is an open source program used to identify similar or duplicate files on Windows systems. It analyzes and compares file content to detect duplicates, providing a GUI and CLI.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: HashMyFiles is a free, open-source software used to calculate checksum hash values for files. It supports various hashing algorithms like MD5, SHA-1, SHA-256, SHA-512, etc. Useful for verifying file integrity and security.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API