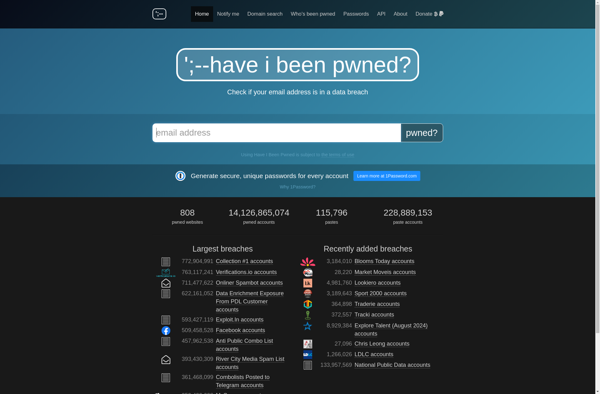
Description: Have I been pwned? is a website that allows internet users to check if their personal data has been compromised by data breaches. It contains a database of breached accounts and allows users to search to see if their email address or phone number appears.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: SkidBase is an open-source computer forensic toolkit for Windows. It is designed to help investigators analyze forensic images efficiently. SkidBase provides various features like viewing event logs, browsing files, extracting data, registry analysis, search tools, and more.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API