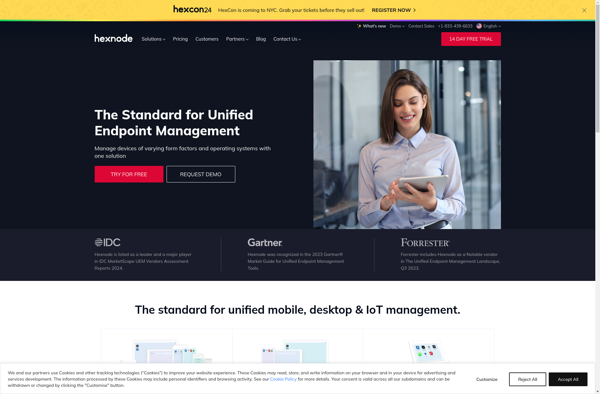
Description: Hexnode UEM is an unified endpoint management solution used to remotely monitor, manage and secure endpoints like laptops, desktops, servers, mobile devices across platforms. It provides features like device management, application management, content management, security management and helps improve productivity.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: SureLock is a cybersecurity software that focuses on providing comprehensive endpoint protection. It utilizes advanced threat detection and remediation capabilities to secure devices across an organization's network.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API