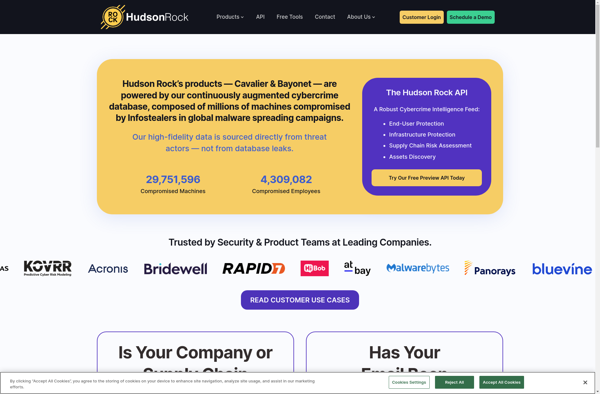
Description: Hudson Rock is an open-source continuous integration and delivery server designed to automate build, test, and deployment pipelines. It supports integrating with source code repositories, running builds and tests, producing reports, and deploying applications.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: ArcSight Enterprise Security Manager (ESM) is a security information and event management (SIEM) platform that provides real-time analysis of security alerts and events. It aggregates data from across the IT infrastructure to monitor for threats, compliance violations, and data breaches.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API