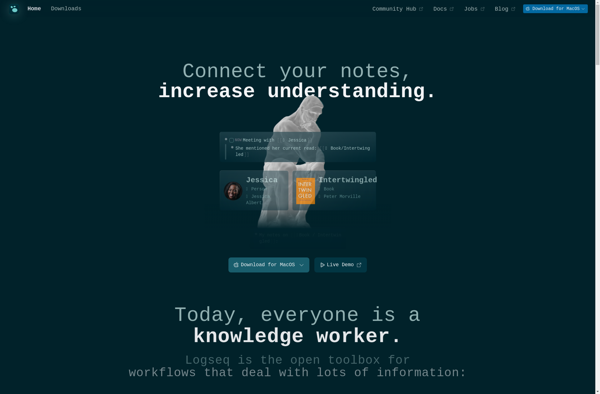
Description: Logseq is an open-source knowledge base and note-taking app built on local-first principles. It allows users to build a second brain to organize notes, tasks, documents and link ideas together in an interconnected graph network.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: Frontdoor is an open-source website vulnerability scanner that helps developers and security teams identify security issues in web applications. It can crawl websites to map all available pages and endpoints, then performs automated scans to detect common vulnerabilities like SQL injection, XSS, insecure configurations, etc.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API