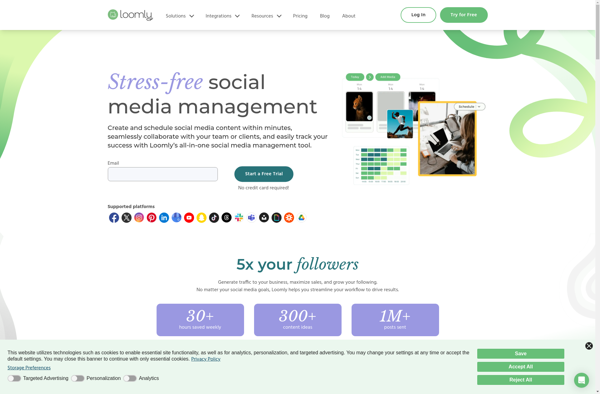
Description: Loomly is a video creation and screen recording tool that allows users to easily capture their screen, record video, edit clips, add annotations and transitions, and share videos. It has an intuitive drag-and-drop interface making video creation simple.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: Vertascan is a vulnerability assessment and penetration testing tool used to identify security weaknesses in web applications and networks. It enables automated scanning to detect misconfigurations, known vulnerabilities, and exposure of sensitive data.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API