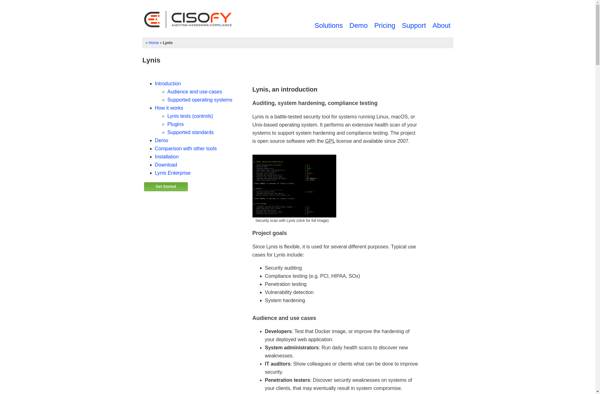
Description: Lynis is an open source security auditing tool for Linux and UNIX-based systems. It performs an in-depth security scan to detect vulnerabilities, provide tips for system hardening, and monitor compliance status.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: Trivy is an open source vulnerability scanner for containers and other artifacts. It scans container images, Git repositories, filesystems and more to detect vulnerabilities and misconfigurations.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API