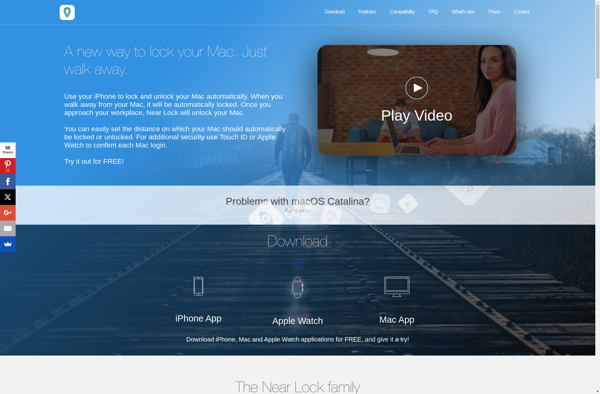
Description: Near Lock is an open-source, self-hosted alternative to Lockwise by Mozilla. It allows users to save and sync passwords securely across devices. As it is self-hosted, it provides more control over data privacy.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: Predator is a download manager and accelerator software for Windows. It allows users to download files faster and manage downloads with advanced features like downloading from multiple connections, scheduling downloads, and downloading videos from streaming sites.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API