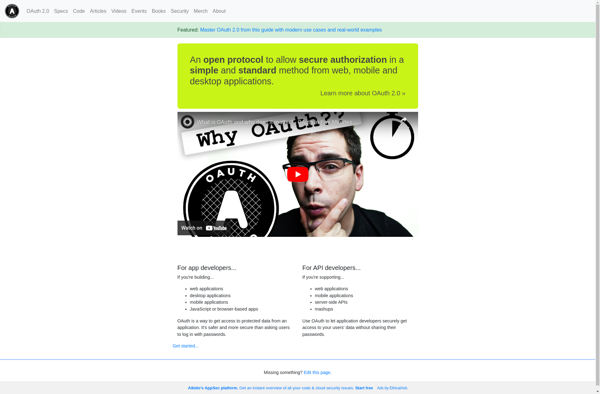
Description: OAuth is an open standard authorization protocol that allows users to grant third-party access to their web resources without sharing their passwords. It allows access delegation without giving away full credentials.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: DandyID is an open-source alternative to Microsoft Active Directory that provides user authentication and authorization services. It allows centralized management of users, groups, permissions, and policies.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API