Description: PEPS is an open-source password manager and secure digital vault. It allows users to securely store passwords, documents, and other sensitive information encrypted with AES-256. PEPS has a simple, clean interface and focuses on security and usability.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
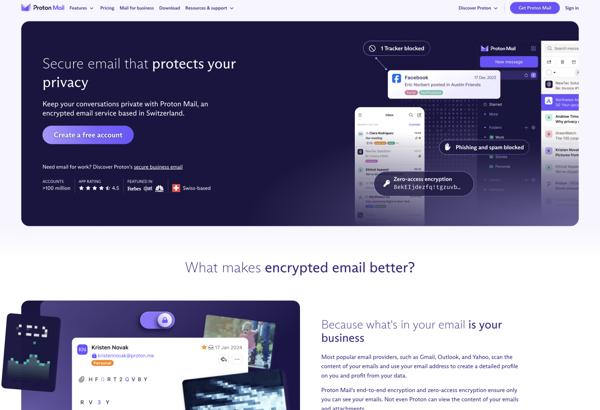
Description: Proton Mail is an encrypted email service based in Switzerland that emphasizes privacy and security. It offers end-to-end encryption, anonymous sign up, self-destructing messages, and more features to protect user data and communications.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API