Description: Privacy Guides is a website that provides guides and recommendations for software, services, and tools focused on protecting privacy and security.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
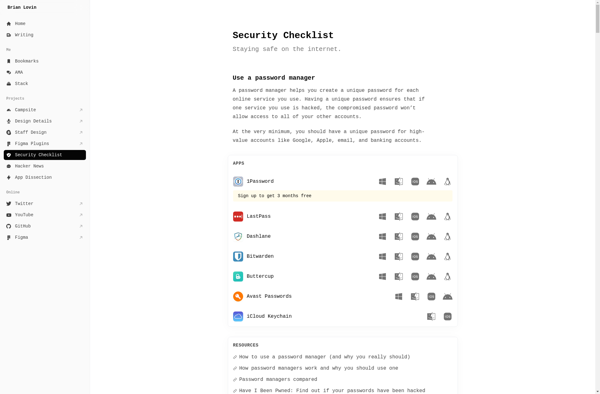
Description: Security Checklist is a software tool that allows users to create customized checklists for securing computers, servers, networks, and other IT infrastructure. It provides templates and guides for implementing security best practices.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API