Description: Procera Networks is a company that provides network intelligence and traffic management solutions for broadband, mobile, and cable network operators. Their products help providers monitor traffic, enforce policies, and improve the quality of service for subscribers.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
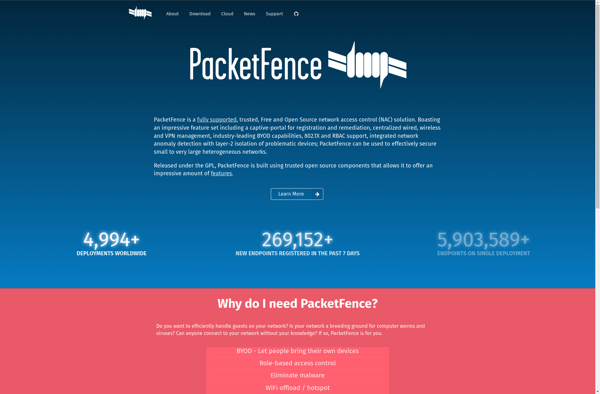
Description: PacketFence is an open source network access control (NAC) system that provides registration, isolation, and remediation services for wired and wireless networks. It helps secure networks by enforcing access policies and isolating unauthorized devices.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API