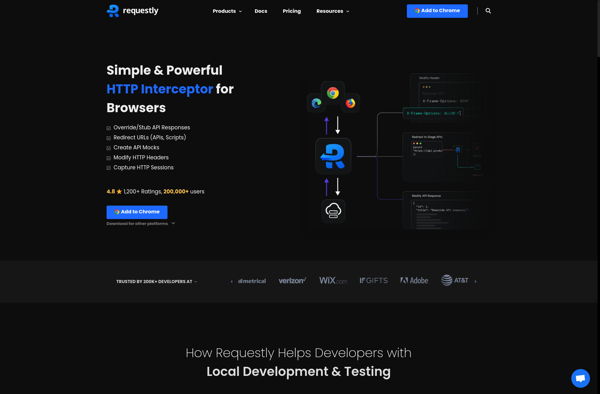
Description: Requestly is a browser extension and web debugging proxy that allows you to modify network requests and responses. It can be used for testing, debugging, automation, mock REST APIs, and modifying requests and responses on the fly.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
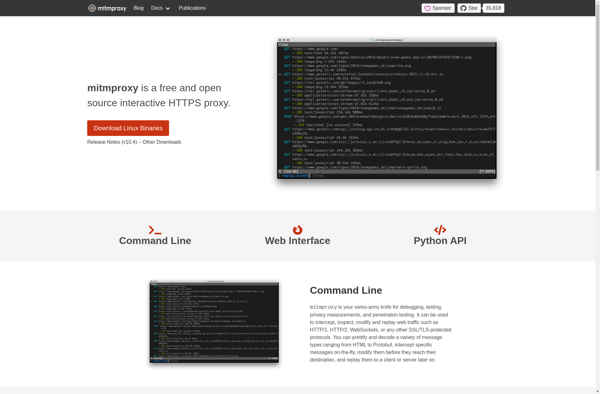
Description: mitmproxy is an open source interactive HTTPS proxy that allows traffic flows to be intercepted, inspected, modified, and replayed. It provides a console interface that allows traffic flows to be inspected and manipulated on the fly.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API