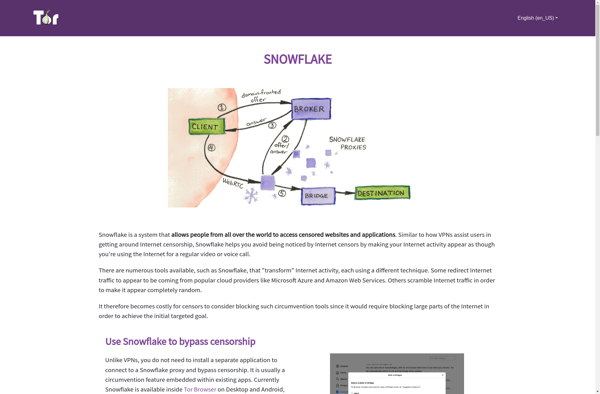
Description: Snowflake Tor is a privacy-focused web browser that routes internet traffic through the Tor network to enhance anonymity and prevent tracking. It aims to make Tor browsing easier for beginners.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: A proxy server acts as an intermediary between client devices and the internet. It serves as a gateway through which internet requests from clients are routed. Proxy servers provide benefits such as caching, filtering content, enhancing security and privacy.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API