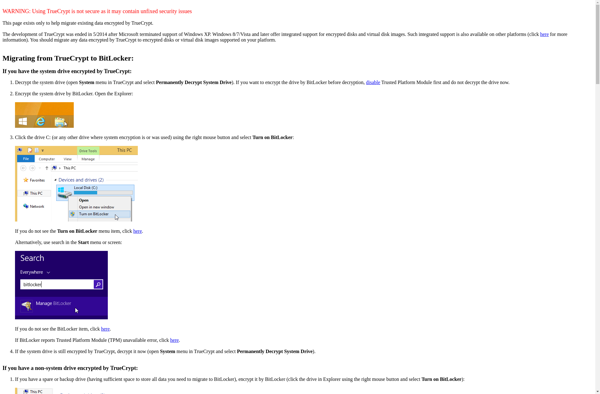
Description: TrueCrypt is an open-source encryption software that can encrypt hard drives and create virtual encrypted disks to store sensitive files and data securely. It works on Windows, Mac OSX and Linux.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: USB Secure is a security software program that password protects USB drives and external hard drives. It uses advanced encryption algorithms to secure data stored on these devices.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API