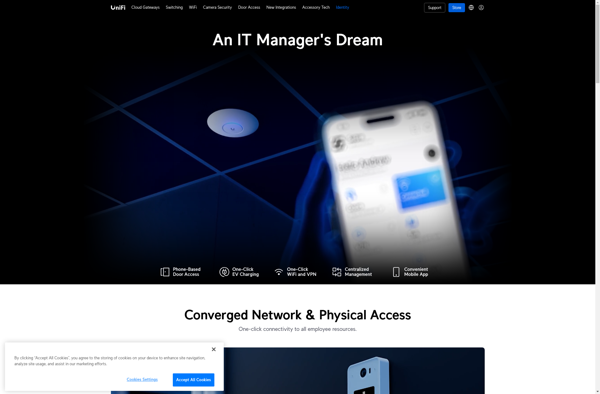
Description: UniFi Identity (UID) is an identity and access management software developed by Ubiquiti Networks. It integrates with UniFi Network and UniFi Protect to provide centralized user authentication and authorization for managing access to Ubiquiti devices and applications.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: HelloID is an identity and access management (IAM) software that centralizes identity, access, governance and administration. It provides single sign-on, multi-factor authentication, identity lifecycle management, access requests and approval workflows.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API