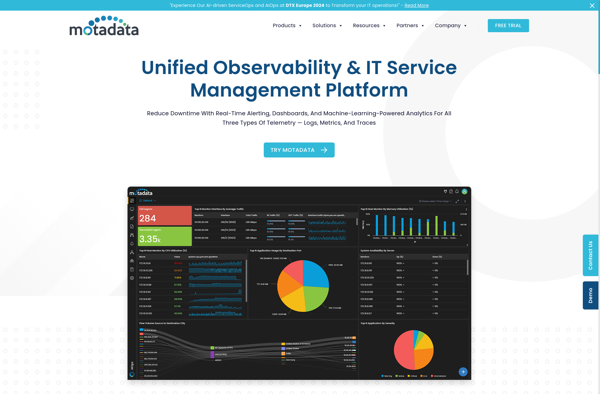
Description: Motadata is a no-code business intelligence and analytics platform that allows users to easily connect data sources, build reports and dashboards, and share analytics insights. It enables data democratization through an intuitive drag-and-drop interface.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: SolarWinds Security Event Manager is a SIEM tool that aggregates log data from across a network to detect threats and analyze security events. It correlates information from various sources for advanced monitoring and compliance reporting.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API