Description: PEBrowse64 Professional is a Windows program used to view and analyze portable executable (PE) files such as EXE, DLL, OCX, SYS, and more. It provides detailed information on the structure and contents of PE files.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
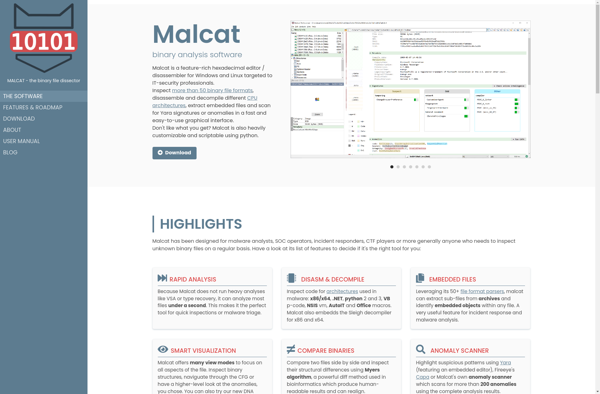
Description: Malcat is an open-source malware analysis tool that allows users to analyze malicious files, extract payloads, perform static analysis, and gather threat intelligence. It has support for a wide variety of file types including PE files, scripts, documents, and memory dumps.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API