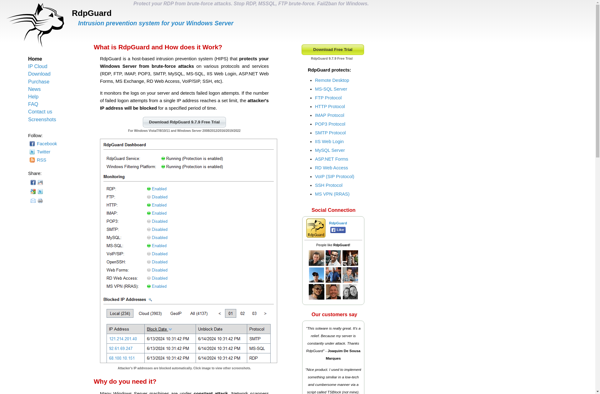
Description: RdpGuard is a remote desktop protection software designed to secure RDP connections against brute force attacks. It includes features like IP blacklisting, account lockouts, advanced authentication protocols, and real-time attack visualization.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: LF Intrusion Detection is an open source intrusion detection system for Linux servers. It monitors network traffic and system logs for suspicious activity and alerts administrators when potential attacks or policy violations are detected.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API