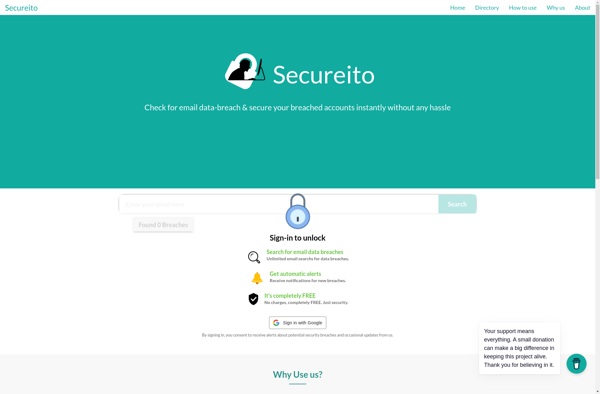
Description: Secureito is a data security and governance platform that helps organizations discover, classify, and protect sensitive data across cloud and on-premises environments. It uses AI and machine learning for automatic data discovery and classification.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
Description: Hacked Leaks Checker is a website that allows you to check if your email address or phone number has been compromised in a data breach. It searches through databases of leaked information and notifies you if your personal data is exposed.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API