Description: Whirlpool File Checker is an open-source utility that computes and matches hash digests of files. It can help verify file integrity and authenticity. The program uses the cryptographic hash function Whirlpool to generate checksums.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
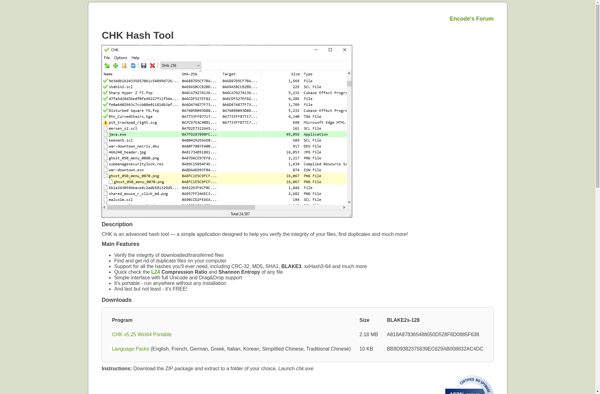
Description: CHK Checksum Utility is a free software utility that calculates and verifies checksums to validate file integrity and detect data corruption. It supports a wide range of hashing and checksum algorithms.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API