Pentest-Tools.com
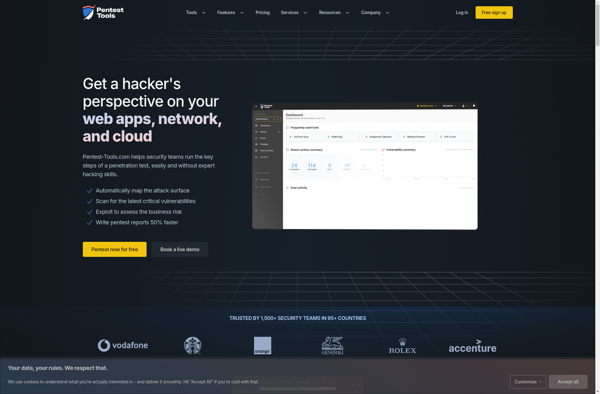
Pentest-Tools.com: Free Online Platform for Penetration Testing and Network Security Auditing Tools
Pentest-Tools.com offers a comprehensive suite of tools for penetration testing and network security auditing, including port scanners, exploits, password crackers, and more, all available for free online use.
What is Pentest-Tools.com?
Pentest-Tools.com is a free online platform that provides penetration testers and network security professionals with various utilities for auditing and exploiting vulnerabilities in networks and systems. It offers a wide range of tools including:
- Port scanners like Nmap to detect open ports and services on servers and devices
- Vulnerability scanners such as Nessus to detect security flaws in networks
- Password crackers like John the Ripper to test password strength
- SQL injection tools to test for SQLi vulnerabilities in web apps
- Packet sniffers for monitoring unencrypted traffic
- Exploits and shells to demonstrate proof of concepts
The interface of Pentest-Tools.com is intuitive and easy to navigate. All tools are online so there is no need for downloads or installations. It offers handy features like the ability to schedule scans and access saved scan reports. The site provides usage guides and tutorials for all tools. It is a valuable platform for information security professionals looking to test and improve the security posture of their organizations.
Pentest-Tools.com Features
Features
- Port scanning tools
- Vulnerability scanners
- Password crackers
- Packet sniffers
- Web application scanners
- Exploitation tools
- Network reconnaissance tools
Pricing
- Free
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best Pentest-Tools.com Alternatives
Top Security & Privacy and Penetration Testing and other similar apps like Pentest-Tools.com
Here are some alternatives to Pentest-Tools.com:
Suggest an alternative ❐Nessus
OpenVAS
Metasploit
Acunetix
Mimikatz
Probely
Nexpose
Detectify

HostedScan Security
Vulners API