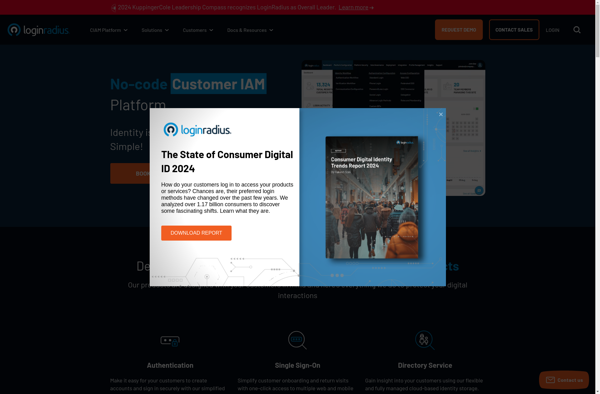
Pomerium
Pomerium: Open-Source Identity-Aware Reverse Proxy
Pomerium enables secure access and control to internal applications and resources with identity-aware proxy features, authenticating requests, enforcing access policies, and encrypting communication.
What is Pomerium?
Pomerium is an open-source identity-aware proxy developed by Pomerium Inc. that provides secure access to internal applications and resources. It acts as a reverse proxy situated between users and applications to handle authentication, authorization, auditing, and encryption.
Some key features of Pomerium include:
- Centralized access control policies to secure internal apps and resources
- Integration with identity providers like Google/OAuth, Active Directory, Okta for authentication
- TLS encryption between Pomerium and internal services to protect data in transit
- Detailed access logs and analytics for auditing and troubleshooting
- Support for headers and claims to convey identity across services
- Cross platform support including Kubernetes, cloud providers, and on-premise
Pomerium focuses on providing zero trust security by verifying user identity and device health before granting the least privileged access. It can help organizations consolidate access management, reduce attack surface, gain visibility, and simplify authentication flows for internal applications. With its identity-centric approach, Pomerium is well suited as a secure front door to internal apps and resources.
Pomerium Features
Features
- Single Sign-On (SSO)
- Access Proxy
- Policy Enforcement
- Identity-Aware Proxy
- Centralized Authentication
- Reverse Proxy
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best Pomerium Alternatives
Top Security & Privacy and Access Control and other similar apps like Pomerium
Here are some alternatives to Pomerium:
Suggest an alternative ❐Keycloak
Auth0
Authelia
Clerk Authentication
AWS Identity and Access Management
LoginRadius