Radare2
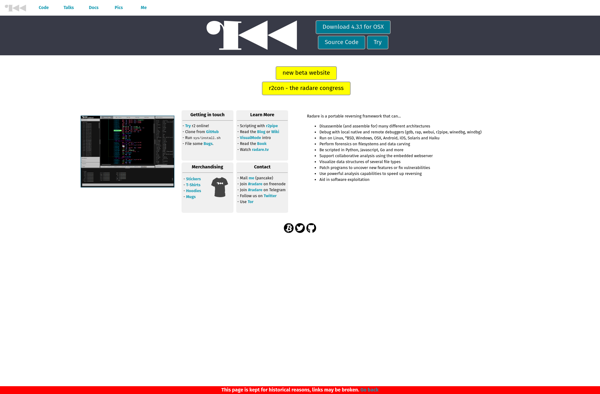
Radare2: Reverse Engineering Framework
Reverse engineering framework with tools for disassembling, debugging, and analyzing binary files, suitable for exploit development, vulnerability research, and malware analysis.
What is Radare2?
radare2 is an advanced, modular, portable reverse engineering framework. It provides a rich set of tools for analyzing binary files, disassembling code, debugging programs, analyzing malware, and more.
Some of the key features of radare2 include:
- Multi-architecture disassembler supporting many Instruction Set Architectures like x86, ARM, MIPS, PowerPC, and more
- Native debugger that works on Linux, macOS, Windows, Android, iOS and BSD
- Advanced code analysis utilizing data flow analysis techniques to identify functions, variables and more
- Graphical tools like the disassembler graph, the mini-graph, and the radial graph for visualizing code flows and call graphs
- Scriptable interface supporting multiple scripting languages like Python, JavaScript, and Lua for automation
- Supports analyzing and patching binaries without the source code across a wide variety of file formats like ELF, Mach-O, PE, and RAW
- Plugin architecture allowing the community to extend functionality and integrate other reverse engineering tools
- Free, open source software (GPLv3 license) with an active developer and user community
In summary, radare2 is one of the most advanced reverse engineering frameworks available. It provides a comprehensive toolset for analyzing and manipulating binary programs catering to reverse engineers, exploit developers, vulnerability researchers, and malware analysts.
Radare2 Features
Features
- Disassembler
- Debugger
- Binary analysis
- Decompiler
- Assembler
- Scripting
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best Radare2 Alternatives
Top Development and Reverse Engineering and other similar apps like Radare2
Here are some alternatives to Radare2:
Suggest an alternative ❐X64dbg
Ghidra

OllyDbg

ImHex
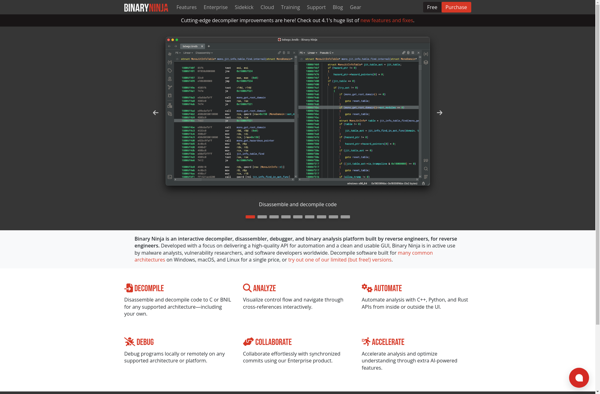
Binary Ninja
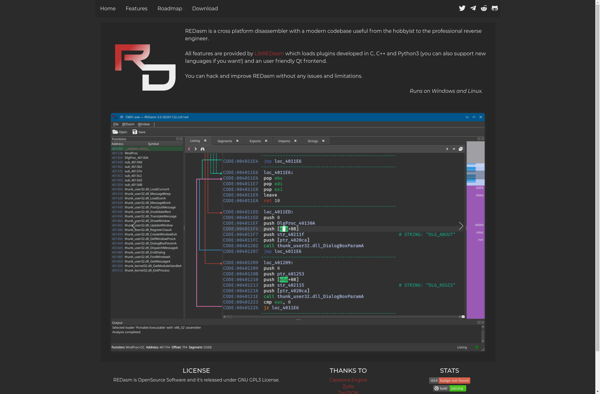
REDasm
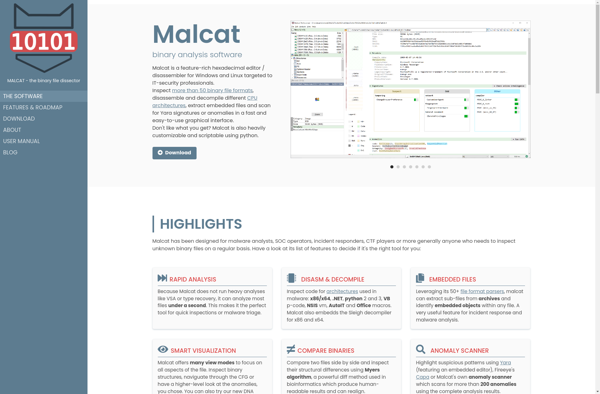
Malcat
GNU Project Debugger
RemedyBG