Tachyon VPN
Tachyon VPN: Fast & Secure Next-Gen VPN
Discover a fast, secure VPN service with next-generation protocol technology for encrypted internet access. With servers in over 50 countries, P2P support, and robust privacy protections.
What is Tachyon VPN?
Tachyon VPN is a virtual private network (VPN) service launched in 2018 that focuses on providing high-speed, secure encrypted internet access to users. It uses its own proprietary VPN protocol called Tachyon Anti-Analysis Tunneling Protocol (TAAP) which is designed to prevent VPN throttling and provide faster speeds.
Some key features of Tachyon VPN include:
- Over 1,000 VPN servers in more than 50 countries around the world.
- Compatible with Windows, Mac, iOS, Android, Linux, routers and more.
- Allows P2P/BitTorrent traffic and works with streaming services like Netflix.
- Strict no-logs policy based in privacy-friendly country.
- Next-gen protocol designed to bypass VPN blocking and throttling.
- Up to 10 multi-logins across devices.
Tachyon VPN has received positive reviews for its fast speeds, extensive server network, and commitment to user privacy. The company is transparent about ownership and operations. Subscriptions come with a 7-day money-back guarantee. Overall, Tachyon VPN aims to provide an optimized, high-performance VPN experience across devices and platforms.
Tachyon VPN Features
Features
- Next-generation WireGuard VPN protocol
- Servers in over 50 countries
- Allows P2P traffic
- AES 256-bit encryption
- Kill switch
- No-logs policy
- Apps for all major platforms
Pricing
- Subscription-Based
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best Tachyon VPN Alternatives
Top Security & Privacy and Vpn and other similar apps like Tachyon VPN
Here are some alternatives to Tachyon VPN:
Suggest an alternative ❐Psiphon
Proton VPN
CyberGhost VPN
Hotspot Shield
Mullvad
SoftEther VPN
Windscribe
TunnelBear
StrongSwan
ZenMate
Shadowsocks

Yggdrasil
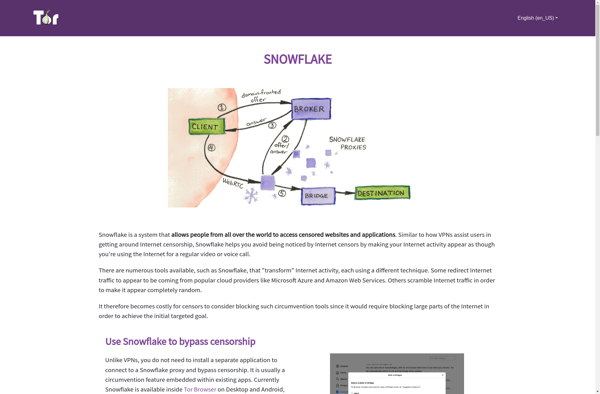
Snowflake Tor