TRITON
TRITON: Dynamic Binary Analysis Framework
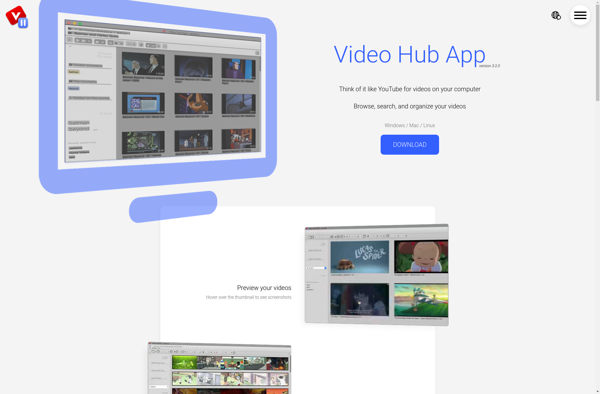
TRITON is a dynamic binary analysis framework that supports binary instrumentation and analysis of Windows, Linux, macOS, and UNIX systems. It enables reverse engineers and malware analysts to unpack malware, perform dynamic unpacking, reconstruct call graphs, trace memory accesses, detect anti-debug and more.
What is TRITON?
TRITON is a dynamic binary analysis and instrumentation framework created by Quarkslab for analyzing Windows, Linux, macOS, and UNIX binaries. It facilitates reverse engineering and malware analysis tasks such as:
- Dynamic unpacking and tracing of packers/protectors
- Reconstruction of accurate call graphs and control flow graphs
- Precise dynamic hooking of program functions and instructions
- Tracing memory accesses, logging Windows API calls
- Detection of anti-debugging and anti-emulation tricks
By inserting instrumentation into binary code, TRITON enables low-level observation and analysis of program execution at runtime. It comes with Python bindings for scripting instrumentation tasks. The open-source framework is designed to be modular and extensible.
TRITON competes with other dynamic binary instrumentation tools like Intel Pin, DynamoRIO, and Frida. It runs on Windows, Linux and macOS systems. The key advantage of TRITON is providing fine-grained control over binary instrumentation through Python scripting as well as native APIs.
TRITON Features
Features
- Dynamic binary instrumentation
- Binary unpacking and analysis
- System call tracing
- Import table reconstruction
- Anti-debugging detection
- Memory access tracing
- Instruction tracing
- Taint analysis
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best TRITON Alternatives
Top Security & Privacy and Reverse Engineering and other similar apps like TRITON
Plex
Jellyfin
Emby
Video Hub App