ArkDasm
ArkDasm: Graphical Disassembler for Windows, Linux, and MacOSs
Graphical disassembler for Windows, Linux, and MacOS, analyzing executable files, object code, bytecode, DLLs, and libraries with intuitive interface
What is ArkDasm?
ArkDasm is a feature-rich graphical disassembler and debugger that allows analyzing and reverse engineering executable files for Windows, Linux, and MacOS operating systems. It can disassemble object code, bytecode, shared libraries, dynamic link libraries, and more to transform machine-readable code into human-readable assembly language.
With an intuitive user interface, ArkDasm makes it easy to inspect executable internals like imports, exports, strings, functions, data sections, etc. Users can navigate seamlessly through the code and data segments. It supports disassembly of x86/x64, ARM, MIPS, PowerPC, and other architectures.
Key features include customizable coloring syntax highlighting, data inspection, commenting code blocks, searching across code or data, analyzing strings and cross-references, scriptable Extensibility features, and other advanced options for experts. ArkDasm generates reports to document the analysis. It has an integrated debugger to dynamite run code execution.
ArkDasm simplifies and accelerates reverse engineering, malware analysis, vulnerability research, and program understanding. It has an engaged user community and active development making it one of the most powerful disassemblers available.
ArkDasm Features
Features
- Graphical user interface
- Disassembles executable files
- Supports Windows, Linux and MacOS
- Analyze and reverse engineer executable code
- Inspect code, data, strings, imports, exports
- Intuitive navigation
Pricing
- Free
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best ArkDasm Alternatives
Top Development and Reverse Engineering and other similar apps like ArkDasm
Here are some alternatives to ArkDasm:
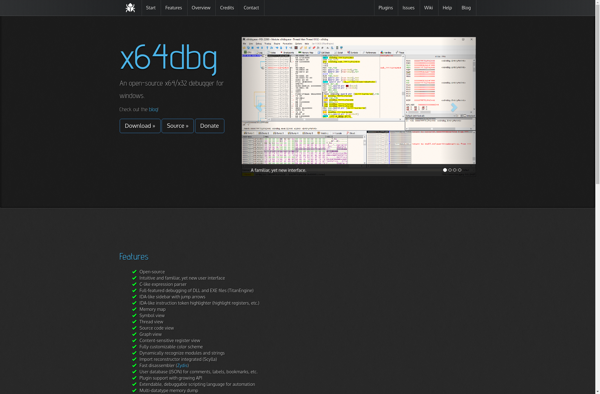
Suggest an alternative ❐X64dbg
Immunity Debugger

OllyDbg

WinDbg
ODA Online Disassembler

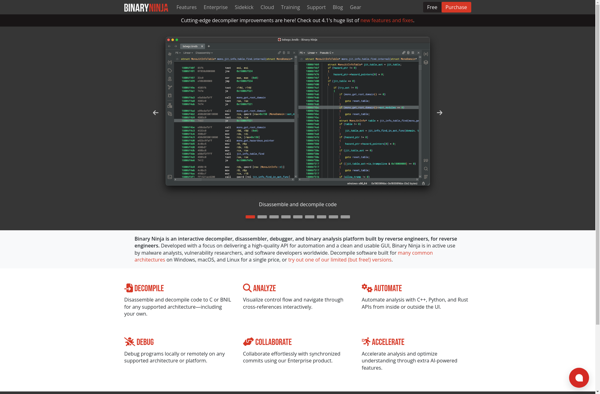
Binary Ninja
Boomerang decompiler
