Proxy Mask
Proxy Mask: Unblocks Blocked Websites with Proxy Servers
Proxy Mask is a Google Chrome and Firefox browser extension that allows users to bypass regional restrictions and access blocked websites using proxy servers. It is a simple VPN add-on that can unblock streaming sites and encrypt connections.
What is Proxy Mask?
Proxy Mask is a Google Chrome and Firefox browser extension that provides access to restricted websites and content by routing connections through proxy servers around the world. It can be used to bypass geographic restrictions, access blocked websites, or mask user identity and location.
Some key features of Proxy Mask include:
- Unblocks streaming sites like Netflix, Hulu, BBC iPlayer, and more by changing IP address to another country
- Allows access to social media, news, or other sites blocked by local internet restrictions
- Hides user's IP address to protect privacy and anonymity online
- Encrypts browsing traffic end-to-end using industry-standard protocols
- Simple one-click activation, no configuration required
- Free and paid subscription plans available
Proxy Mask installs as an add-on within the Chrome or Firefox browser. With a click of a button, it connects through remote proxy servers to relay web traffic. This fools websites into thinking the user is located elsewhere. The extension supports proxy connections from over 20 different countries.
The free version has limited bandwidth and lacks certain advanced features. Upgrading to premium adds support for streaming in HD quality, faster speeds, expanded country connections, and simultaneous device usage.
Proxy Mask Features
Features
- Bypass regional restrictions
- Access blocked websites
- Use proxy servers
- Simple VPN add-on
- Unblock streaming sites
- Encrypt connections
Pricing
- Free
Pros
Cons
Reviews & Ratings
Login to ReviewThe Best Proxy Mask Alternatives
Top Security & Privacy and Vpn & Proxy and other similar apps like Proxy Mask
Here are some alternatives to Proxy Mask:
Suggest an alternative ❐Psiphon
Proton VPN
Tor Browser

Hotspot Shield
Mullvad
Matrix.org
Windscribe
ZenMate
IPFS

Shadowsocks

ReQrypt
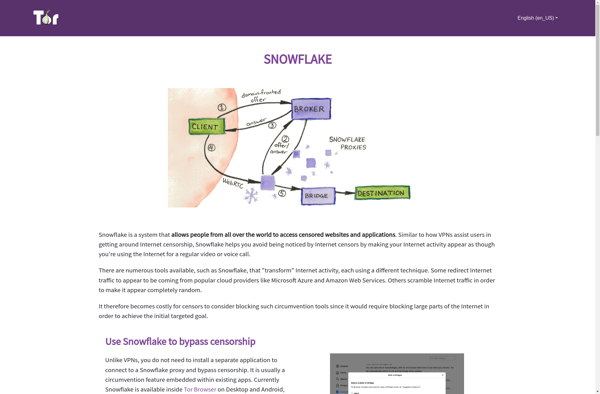
Snowflake Tor
BitDust

Tor Bridges Collector