Torifier
Torifier: Open Source Anonymity Tool
Torifier routes internet traffic through the Tor network for online anonymity and censorship circumvention, hiding your IP address
What is Torifier?
Torifier is an open source application developed by Australia's Navy that routes internet traffic through the Tor network to provide online anonymity and circumvention of network censorship. It works by forcing all TCP traffic on the computer to be routed through the Tor network, which encrypts and bounces communications through a series of Tor relays to hide the user's IP address and location.
Key features of Torifier include:
- Hides user's IP address and physical location to provide anonymity while web browsing
- Allows access to onion services hidden Tor sites and apps (.onion sites)
- Circumvents censorship and blocked websites by routing through the Tor network
- Compatible with Linux, macOS, and Windows operating systems
- Open source software published under the GNU GPLv2 license
- Command-line interface allows advanced configuration options
Torifier is often used by journalists, activists, and those seeking privacy and security online to communicate anonymously and evade government censorship. The routing through multiple Tor nodes provides better privacy than proxy servers. However, Torifier can slow down internet speeds due to the indirect routing. It is developed and managed as a community project by open source advocates focused on internet freedom and privacy.
Torifier Features
Features
- Anonymity and privacy protection
- Circumvention of internet censorship
- Routing of all internet traffic through the Tor network
- Automatic configuration and setup of Tor
- Support for various operating systems (Windows, macOS, Linux)
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best Torifier Alternatives
Top Security & Privacy and Anonymity & Circumvention and other similar apps like Torifier
Here are some alternatives to Torifier:
Suggest an alternative ❐Tor Browser

Mullvad
Freegate
TunnelBear
I2P

FreePN
AirVPN

ProxAllium
Your Freedom
Yggdrasil
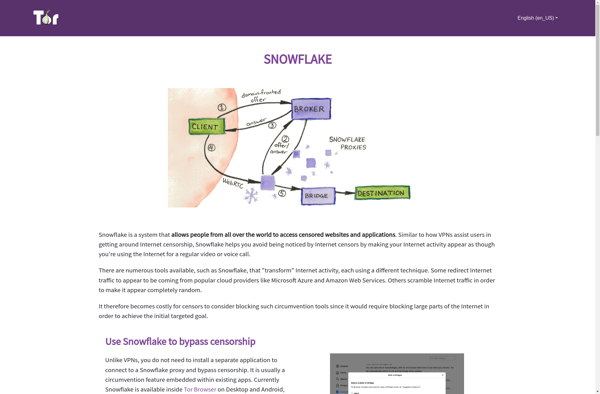
Snowflake Tor