I2P

I2P: Anonymous Network Layer
I2P is an anonymous network layer that allows applications to send messages to each other pseudonymously and securely. It is an overlay network that uses cryptography and tunnels to hide the identity and location of users.
What is I2P?
I2P (Invisible Internet Project) is an anonymous network layer designed to allow applications to communicate securely and privately. Some key aspects of I2P include:
- Anonymity - I2P obscures the identity and location of users by routing traffic through an overlay network of peer-to-peer tunnels.
- End-to-end encryption - Messages sent through I2P are encrypted from the sender to endpoint, protecting communication content confidential.
- Censorship resistance - The decentralized nature of I2P makes it resistant to censorship and surveillance.
- Open source - I2P is developed as a free and open source project maintained by volunteers.
I2P allows people to host services like websites, chat servers, and file sharing safely by shielding the server operator and clients from surveillance. Some common applications built on I2P include I2P-Bote (secure email), Susimail (webmail), and I2P torrent tracker. The anonymity and privacy properties make I2P suitable for those needing high security and resistance against monitoring.
I2P Features
Features
- Anonymous communication
- End-to-end encryption
- Distributed network
- Hidden services
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best I2P Alternatives
Top Security & Privacy and Anonymous Communication and other similar apps like I2P
Here are some alternatives to I2P:
Suggest an alternative ❐Tor Browser

V2Ray
The Web
Freenet
Freegate
Matrix.org
Shadowrocket
Hide.me
Spotflux
Advanced Onion Router
CacheBrowser
IPFS

Hide My IP
ZeroMe
Onion.ly
Shadowsocks

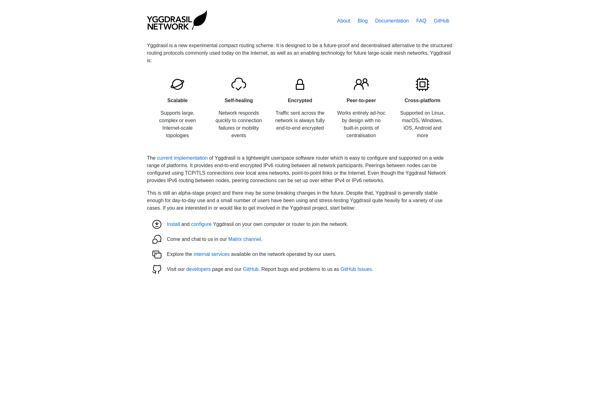
Yggdrasil
Decentralized Internet
OnionCat
Torifier
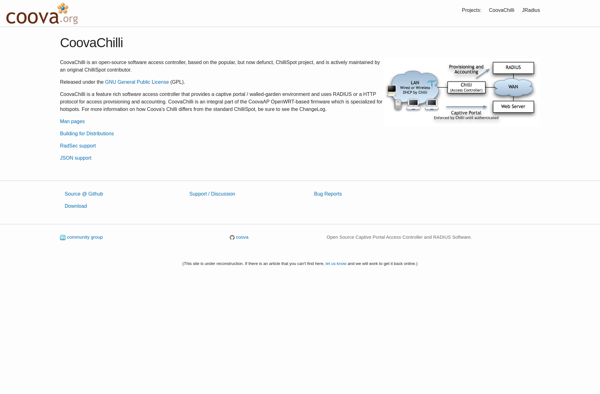
CoovaChilli
Lokinet
Unblock All
Vidalia

Demonsaw
GNUnet
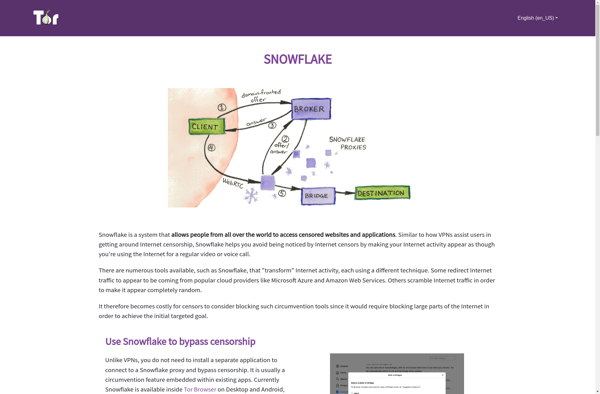
Snowflake Tor
Unirises VPN
Ninux
NetShade
Cjdns
OneSwarm

Alliance P2P
IPZN
ECnet
Cryptostorm
Project Maelstrom
VPNMaster
BitDust

Mith.co
Anonine
LibertyHero
Mask Surf

Expat Shield
Hide IP NG
Stealthnet
IP Privacy
UltraVPN
Tor Control Panel
Absentis Web Cache Service

Torxy
Netsukuku
Osiris SPS
FBVPN
Anomos
CCNx
Kommute