Unirises VPN
Unirises VPN: Fast & Secure Global Internet Access
Unirises VPN provides encrypted connections for a secure internet experience, with servers in 60+ countries and support for P2P traffic, unlimited bandwidth, and more.
What is Unirises VPN?
Unirises VPN is a virtual private network service that aims to provide security and privacy protection when browsing the internet. It works by creating an encrypted tunnel between your device and one of their servers, hiding your real IP address and routing your traffic through the VPN server.
Some key features of Unirises VPN include:
- Servers in over 60 countries around the world, allowing you to bypass geolocation restrictions on certain content.
- Supports P2P file sharing and torrenting on certain servers.
- Unlimited bandwidth so you can download or stream as much as you want.
- 256-bit AES encryption to securely tunnel your data.
- A no-logs policy stating they do not track or store user activity data.
- Apps for Windows, Mac, iOS, Android, and Linux devices.
- Allows up to 6 simultaneous connections with one account.
Unirises VPN has received decent reviews praising its speed and reliability. One downside is the smaller server network compared to top providers. But it remains a good mid-tier VPN option with some useful features for security-focused users or torrenters.
Unirises VPN Features
Features
- Encrypted internet connection
- Servers in over 60 countries
- Allows P2P traffic
- Unlimited bandwidth
- Kill switch
- Split tunneling
- SOCKS5 proxy
Pricing
- Subscription-Based
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best Unirises VPN Alternatives
Top Security & Privacy and Vpn and other similar apps like Unirises VPN
Here are some alternatives to Unirises VPN:
Suggest an alternative ❐Psiphon
Proton VPN
Tor Browser

Hotspot Shield
Mullvad
Freenet
Windscribe
TunnelBear
I2P

Shadowsocks

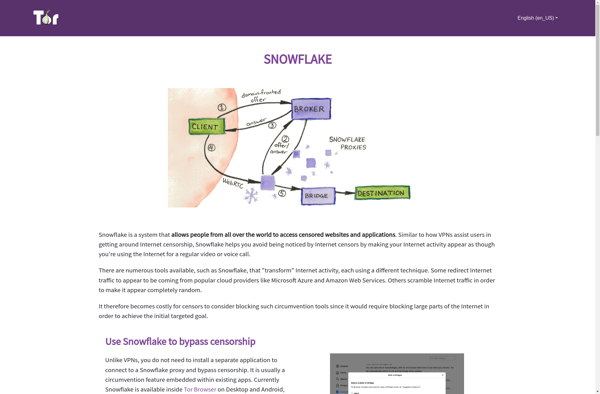
Snowflake Tor