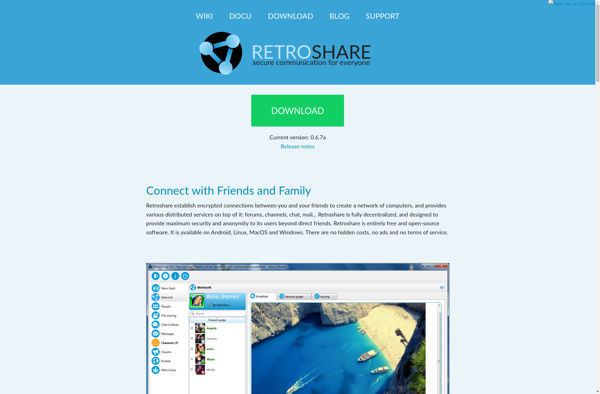
Stealthnet
Stealthnet: Decentralized VPN for Secure Anonymous Network Connections
Stealthnet protects user privacy and provides secure internet access, masking your identity and browsing history while using a decentralized VPN service.
What is Stealthnet?
Stealthnet is a decentralized VPN service designed to provide private and anonymous internet access. It utilizes peer-to-peer networking and encryption protocols to route internet traffic through multiple nodes in the Stealthnet network.
Some key features of Stealthnet include:
- Masks your IP address and location to protect your privacy
- Encrypts your browsing data end-to-end to prevent surveillance or tracking
- No activity or connection logs are maintained by the network nodes
- Uses multilayered encryption and authentication for securing network traffic
- Leverages a distributed hash table for network addressing instead of centralized servers
- Community-driven open source platform that is transparent and self-scaling
Stealthnet aims to give users control over their privacy and anonymity online by providing a secure way to access the internet without fear of censorship or monitoring. The decentralized architecture means there is no central point of failure for surveillance or attack.
Stealthnet Features
Features
- Decentralized VPN
- Anonymous network connections
- Protects user privacy
- Provides secure internet access
- Masks user identity
- Masks browsing history
Pricing
- Subscription-Based
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best Stealthnet Alternatives
Top Security & Privacy and Vpn and other similar apps like Stealthnet
Here are some alternatives to Stealthnet:
Suggest an alternative ❐I2P

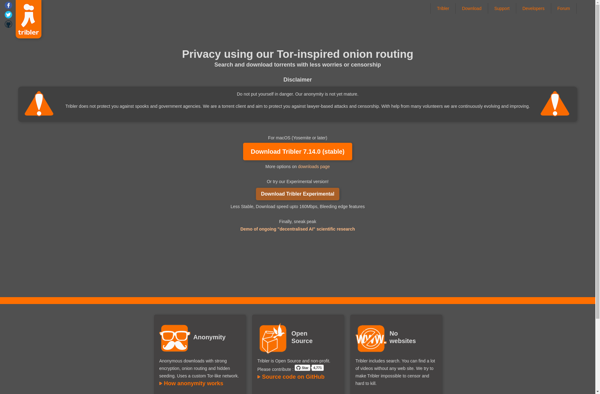
Tribler
Calypso

I2pd (I2P Daemon)

GNUnet
Perfect Dark
ANts P2P