GNUnet
GNUnet: Secure Peer-to-Peer Networking Framework
A decentralized network for secure data exchange, replacing traditional internet architecture with censorship-resistant services like content distribution and privacy-preserving transactions.
What is GNUnet?
GNUnet is an open-source framework for decentralized, peer-to-peer networking designed to provide secure communication and basic services without the need for centralized servers. Developed as part of the GNU Project, GNUnet aims to replace the current client-server model of the internet with a more decentralized architecture.
At its core, GNUnet provides the building blocks for creating secure, anonymous peer-to-peer applications. This includes encrypted communication between peers, censorship-resistant file-sharing, a distributed data store for global name resolution, and privacy-preserving transactions. The goal is to offer basic infrastructure and services like content distribution, messaging, and payments without relying on third parties.
From a technical standpoint, GNUnet consists of multiple components and layers that work together. This includes transport encryption, peer discovery services, distributed hash tables for data storage, and economic protocols for incentive management. Peers connect in a mesh network topology and communicate directly rather than routing everything through central servers.
Overall, GNUnet brings the ideas of decentralization, security and privacy to network communication and applications. With its censorship-resistant architecture and cryptographic identity management, it reduces reliance on existing communication channels and infrastructure providers. This makes it more resistant against surveillance, censorship and service disruption while putting users back in control of their data and communication.
GNUnet Features
Features
- Decentralized network architecture
- Censorship resistance
- Anonymous and secure communication
- File sharing
- Distributed data storage
- Cryptocurrency transactions
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best GNUnet Alternatives
Top Network & Admin and Decentralized Networks and other similar apps like GNUnet
Here are some alternatives to GNUnet:
Suggest an alternative ❐UltraSurf
Freenet
Freegate
Matrix.org
I2P

IPFS

ZeroMe
Onion.ly
Tunngle
Shadowsocks

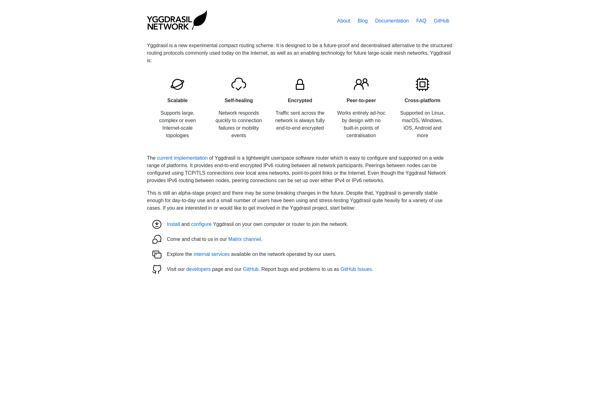
Yggdrasil
Decentralized Internet
Touch VPN
OnionCat
CoovaChilli
Vidalia

Demonsaw
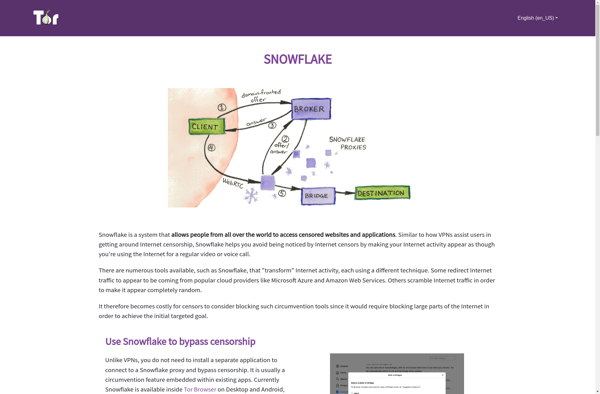
Snowflake Tor
MuWire
Ninux
Cjdns
ECnet
Telehash

Project Maelstrom
Babel (protocol)
VPNMaster
BitDust

Mith.co
Perfect Dark
OLSR (Optimized Link State Routing)
LibertyHero
Qaul
NotMyIP
SailfishVPN
Supernet
Stealthnet
IP Privacy
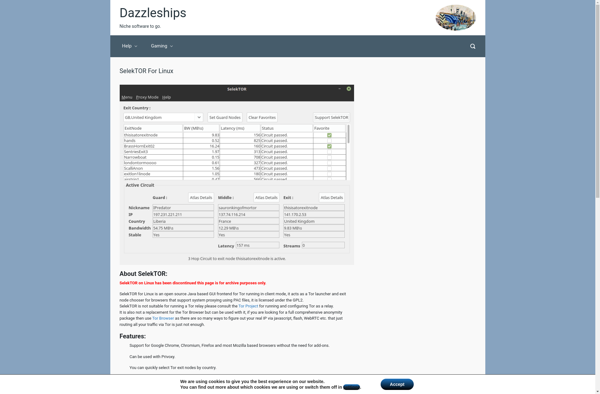
SelekTOR
UltraVPN
Phex
Netsukuku
Osiris SPS
FBVPN
SMesh
Anomos
FireTweet