I2pd (I2P Daemon)

i2pd: Open-Source I2P Daemon for Secure Anonymous Network Access
i2pd is an open-source C++ implementation of the I2P anonymous network. It is designed to be a lightweight, fast, and secure way to access I2P services and route anonymous traffic.
What is I2pd (I2P Daemon)?
i2pd (I2P Daemon) is an open-source C++ implementation of the I2P anonymous network that focuses on security, efficiency, and ease of use. Unlike the original Java I2P implementation, i2pd is designed to be lightweight, fast, and efficient.
Some key features of i2pd include:
- End-to-end encrypted anonymous IPv6 tunnels
- Distributed database and peer selection
- Built-in protocols for popular applications like IRC, email, and BitTorrent
- API for developers to build new applications
- Extensive peer-review and cryptography to ensure anonymity
- Active development community focused on security and anonymity
i2pd allows users to access and participate in the I2P anonymous network to browse .i2p websites, host anonymous services, communicate securely, share files, and more - all while protecting the user's privacy from surveillance or traffic analysis.
Overall, i2pd is a robust, efficient, and easier-to-use implementation of I2P that brings anonymous, cryptographic networking to more people.
I2pd (I2P Daemon) Features
Features
- Anonymous networking
- End-to-end encryption
- Distributed network
- Hidden services
- Tunnels for inbound and outbound connections
- NAT traversal
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best I2pd (I2P Daemon) Alternatives
Top Security & Privacy and Anonymity Networks and other similar apps like I2pd (I2P Daemon)
Here are some alternatives to I2pd (I2P Daemon):
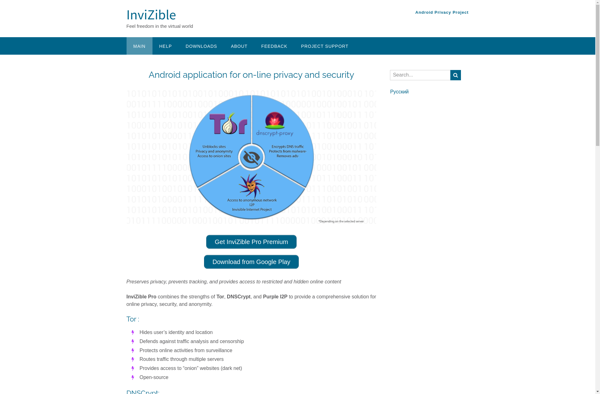
Suggest an alternative ❐InviZible Pro
Onion.ly
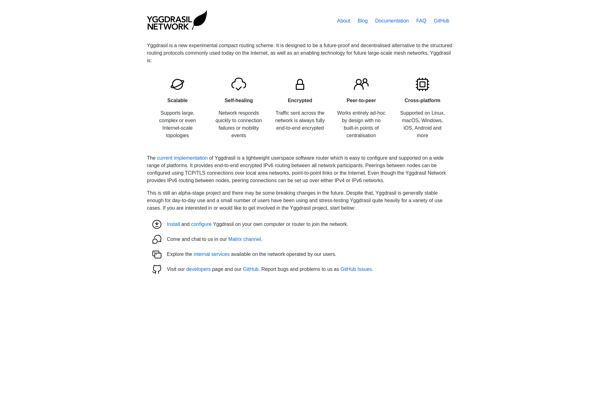
Yggdrasil
Decentralized Internet
OnionCat
CoovaChilli
Demonsaw
Ninux
Cjdns
BitDust
