V2Ray
V2Ray: Open-Source Network Proxy Tool
V2Ray is an open-source network proxy tool that helps bypass firewall restrictions. It supports multiple protocols and allows circumventing IP blocking and traffic throttling.
What is V2Ray?
V2Ray is an open-source, cross-platform proxy software tool primarily used to bypass firewalls and network restrictions. It supports multiple transport protocols and encryption methods to route network traffic while concealing the true origin and destination.
Some key features of V2Ray include:
- Helps bypass geo-restrictions and censorship by IP blocking, DNS poisoning, etc.
- Supports various protocols like VMess, Shadowsocks, SOCKS, HTTP proxy, and more
- Uses industry-standard encryption algorithms like AES and ChaCha20 to secure traffic
- Offers a modular plugin design for customizability and flexibility
- Available across Windows, Mac, Linux, Android, iOS platforms
- Open-source codebase with active developer community
V2Ray routes internet traffic through intermediary servers to bypass firewalls while masking the identities of senders and recipients. This allows users in restrictive networks to access blocked content and websites. With robust encryption and active development, V2Ray is regarded as one of the most versatile proxy tools.
V2Ray Features
Features
- Proxying capability for bypassing firewalls
- Multiple protocol support including VMess, Shadowsocks, SOCKS and HTTP proxy
- Traffic routing and muxing
- TLS encryption
- CDN support
- Plugin system for extending functionality
Pricing
- Open Source
- Free
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best V2Ray Alternatives
Top Security & Privacy and Vpn & Proxy Tools and other similar apps like V2Ray
Here are some alternatives to V2Ray:
Suggest an alternative ❐Psiphon
Proton VPN
CyberGhost VPN
Hotspot Shield
Mullvad
Freenet
Holy Unblocker
Windscribe
TunnelBear
I2P

Amnezia VPN
Stunnel
Your Freedom
Shadowsocks

Gobetween

PD-Proxy
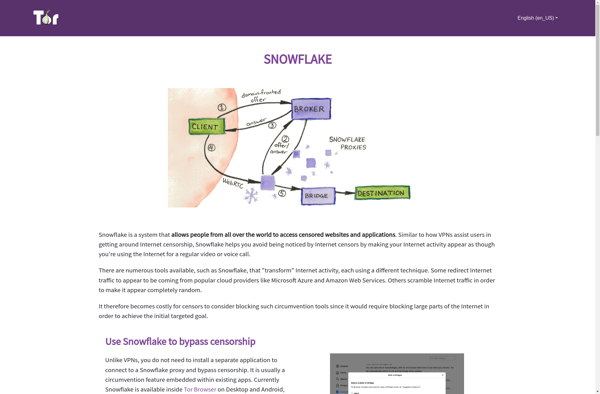
Snowflake Tor
WallProxy
GAppProxy