Description: IPQ BDB is a database software designed for storing and managing large volumes of IP network traffic data. It allows efficient storage and analysis of network metadata.
Type: Open Source Test Automation Framework
Founded: 2011
Primary Use: Mobile app testing automation
Supported Platforms: iOS, Android, Windows
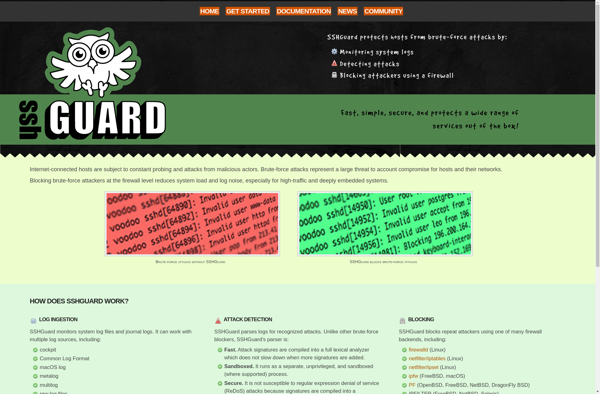
Description: SSHGuard is an intrusion prevention software for Linux and BSD systems. It works by detecting automated brute force attacks against SSH servers and blocks attackers' IP addresses with advanced firewall rules. It is lightweight, easy to configure, and helps harden SSH servers against attacks.
Type: Cloud-based Test Automation Platform
Founded: 2015
Primary Use: Web, mobile, and API testing
Supported Platforms: Web, iOS, Android, API