SSHGuard
SSHGuard: Lightweight Intrusion Prevention for Linux & BSD
Detects automated brute force attacks on SSH servers, blocking attackers' IP addresses with advanced firewall rules, and helps harden SSH servers against attacks.
What is SSHGuard?
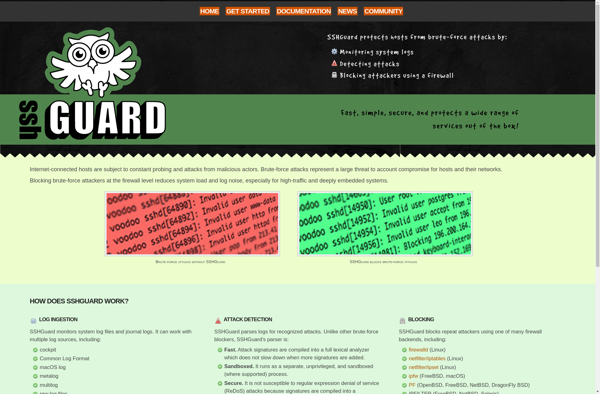
SSHGuard is an open source intrusion prevention software designed to protect Linux and BSD based systems that run SSH servers. It analyzes system log files in real-time to detect attacks such as brute force attempts to guess passwords, scans searching for SSH server vulnerabilities, and other common attacks targeting systems with SSH ports exposed to the internet.
SSHGuard works by leveraging the power of IPtables firewall rules on Linux and PF firewall on BSD systems. When an attack is detected via the logs, SSHGuard will immediately block the attacker's IP address automatically at the firewall level. The ban can be configured to expire after a set amount of time or stay permanently blocked depending on preferences.
Some key capabilities and benefits of SSHGuard include:
- Lightweight software with minimal system resource usage
- Easy installation and configuration, no need to modify SSH server configs
- Real-time attack detection by parsing auth and firewall logs
- Automatic blocking at firewall level when attacks are seen
- Predefined ban thresholds for common vectors like SSH brute force
- Configurable ban duration, from temporary to permanent blocking
- Whitelist to exclude trusted IP ranges from ever being blocked
Overall, SSHGuard serves as an integral layer of defense to significantly enhance the security of SSH server environments. It prevents attackers from completing brute force and scanning attacks, stopping threats at the network perimeter while requiring minimal setup and ongoing management.
SSHGuard Features
Features
- Detects and blocks automated brute force attacks against SSH servers
- Implements advanced firewall rules to block attackers' IP addresses
- Lightweight and easy to configure
- Helps harden SSH servers against attacks
- Supports Linux and BSD systems
Pricing
- Open Source
Pros
Cons
Features
- Automated detection and blocking of brute-force attacks against SSH servers
- Advanced firewall rule management to block attackers' IP addresses
- Lightweight and easy to configure
- Helps harden SSH servers against attacks
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best SSHGuard Alternatives
Top Security & Privacy and Intrusion Prevention and other similar apps like SSHGuard
Here are some alternatives to SSHGuard:
Suggest an alternative ❐Fail2ban
RdpGuard
IPBanPro

LF Intrusion Detection
E.guardo Smart Defender
SpyLog
Denyhosts

Win2ban
HeatShield
Hookem-Banem
Pyruse

IPQ BDB