Fail2ban
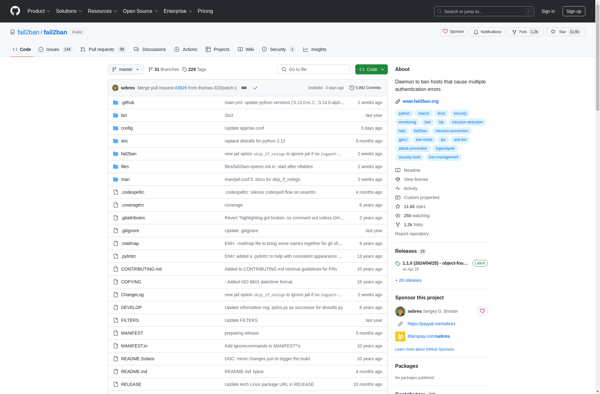
Fail2ban: Open Source Intrusion Prevention for Brute-Force Attacks
Fail2ban is an open source intrusion prevention software framework that protects computer servers from brute-force attacks by banning IP addresses that attempt too many login failures.
What is Fail2ban?
Fail2ban is an open source intrusion prevention software framework designed to protect computer servers from brute-force attacks. It works by monitoring log files for signs of suspicious activity and banning IP addresses that attempt too many failed login attempts.
Once Fail2ban detects multiple failed login attempts from the same IP address over a defined period of time, it updates firewall rules to reject any further connection attempts from that IP for a specified amount of time. This helps prevent brute-forcing of passwords and denies access to server resources for suspicious clients.
Some key features of Fail2ban include:
- Monitoring of log files from services like SSH, Apache, Nginx, FTP, SMTP, and more
- Ability to define complex ban rules and actions
- Support for IPv4 and IPv6
- Flexible configuration to tune for specific use cases
- Plugin architecture to extend functionality
Fail2ban is available for Linux and UNIX based systems. It helps administrators secure their servers by reducing the risk and impact of password guessing attacks. The program is highly customizable through editing of configuration files and writing custom scripts and plugins.
Fail2ban Features
Features
- Bans IP addresses that attempt too many failed logins
- Monitors log files for failed login attempts
- Highly configurable to work with many services like SSH, SMTP, HTTP, etc
- Easy to install and configure
- Written in Python
- Cross-platform - works on Linux, BSD, and some Unix systems
Pricing
- Open Source
Pros
Cons
Reviews & Ratings
Login to ReviewThe Best Fail2ban Alternatives
Top Security & Privacy and Intrusion Prevention and other similar apps like Fail2ban
RdpGuard
IPBanPro

LF Intrusion Detection
AiP Defense

Cyberarms Intrusion Detection and Defense
E.guardo Smart Defender
EvlWatcher
SpyLog
Denyhosts

CrowdSec
SSHGuard
Win2ban
HeatShield
Hookem-Banem
Pyruse

IPQ BDB