BloodHound
BloodHound: Open Source Security Tool
Analyze Active Directory environments and identify potential attack paths with BloodHound, a powerful open source security tool.
What is BloodHound?
BloodHound is an open source security software used to analyze Active Directory environments to find relationships and paths between different Active Directory objects and identify potential ways for an attacker to escalate privileges and move laterally within the network.
It uses graph theory to analyze the extracted data, map out the relationships, and highlight possible attack paths that could allow an attacker to compromise privileged accounts. BloodHound does not perform any exploitation itself, it is used as a security analysis tool.
Some key features and capabilities of BloodHound:
- Identifies shortest path to privilege escalation such as finding the shortest path from a regular user account to a domain admin account
- Highlights accounts with most admin-like privileges to prioritize security hardening efforts
- Models the impact of implementing various security policies to identify policy gaps
- Integrates with other tools through APIs and data export in multiple formats
- Intuitive and flexible graphical interface to visualize attack paths
BloodHound is commonly used along with other offensive security tools as part of red team planning and identifying areas of improvement to strengthen the overall Active Directory security posture.
BloodHound Features
Features
- Graph database showing relationships between Active Directory objects
- Identifies privilege escalation paths and access control vulnerabilities
- Visualizes effective permissions and trusts
- Integrates data from LDAP and Kerberos
- Built on Neo4j graph database
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best BloodHound Alternatives
Top Security & Privacy and Active Directory Security and other similar apps like BloodHound
Here are some alternatives to BloodHound:
Suggest an alternative ❐Metasploit
Mimikatz
Cobalt Strike
ZoomEye
Social-Engineer Toolkit
Nexpose
Sn1per Professional
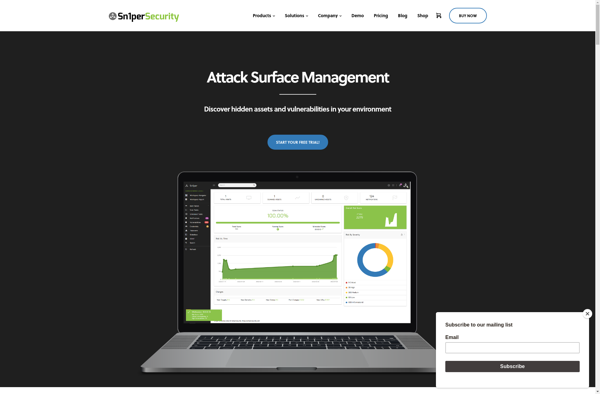
Immunity CANVAS
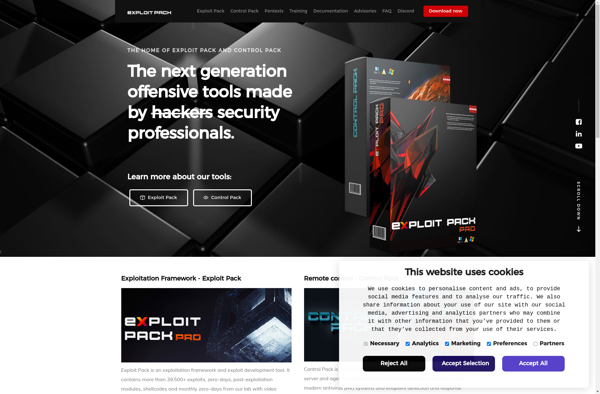
Exploit Pack
Andspoilt