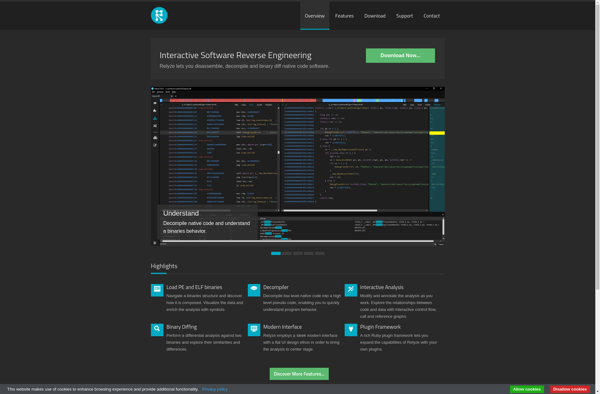
Relyze
Relyze is a cybersecurity software that provides continuous validation of an organization's security controls. It automates asset discovery, security control assessments, and compliance reporting.
Relyze: Cybersecurity Software
Automated cybersecurity software for continuous validation of security controls, asset discovery, and compliance reporting.
What is Relyze?
Relyze is a comprehensive cybersecurity software platform designed to help organizations continuously validate their security controls and demonstrate compliance. It features:
- Automated asset discovery to maintain an up-to-date inventory of all IT assets.
- Ongoing security control assessments based on industry frameworks like NIST, PCI DSS, and HIPAA.
- Compliance reporting across regulatory mandates and internal policies.
- Remediation tracking and workflow automation capabilities.
- Custom risk scoring based on CVSS and customizable frameworks.
- Data connectivity across existing security tools for centralized visibility.
Relyze aims to save security teams significant time by automating manual processes while providing a living view of their security and compliance posture. With repeatable assessments and compliance evidence readily available, organizations can make data-driven decisions to reduce risk. The software is cloud-native and suited for mid-size to large enterprises.
Relyze Features
Features
- Continuous validation of security controls
- Automated asset discovery
- Automated security control assessments
- Automated compliance reporting
Pricing
- Subscription-Based
Pros
Automates tedious security processes
Provides continuous visibility into security posture
Simplifies compliance reporting
Can integrate with existing tools and frameworks
Cons
Can be complex to set up and configure initially
Limited customization options
Reporting not as robust as some alternatives
Official Links
Reviews & Ratings
Login to ReviewThe Best Relyze Alternatives
Top Security & Privacy and Vulnerability Management and other similar apps like Relyze
Here are some alternatives to Relyze:
Suggest an alternative ❐PE Explorer
PE Explorer is a feature-rich portable executable (PE) file viewer, editor, analyzer, and debugger for Windows. It enables developers, reverse engineers, and malware analysts to examine the structure and components of EXE, DLL, OCX, SYS, and other PE file formats in great depth.With PE Explorer, you can view and edit...

ODA Online Disassembler
ODA Online Disassembler (ODA) is a free online disassembly tool that runs fully in your web browser without requiring any downloads or installations. It allows you to easily disassemble executable files such as EXE, DLL, OCX, CPL, SYS, OBJ, LIB, etc. for a variety of processor architectures including x86, amd64,...

CFF Explorer
CFF Explorer is a powerful tool for examining, editing, and reverse engineering executable files in the Common File Format (CFF). It supports a wide range of file types including EXE, DLL, OCX, SYS, LIB, and more.Some of the key features of CFF Explorer include:Viewing the full structure and hierarchy of...
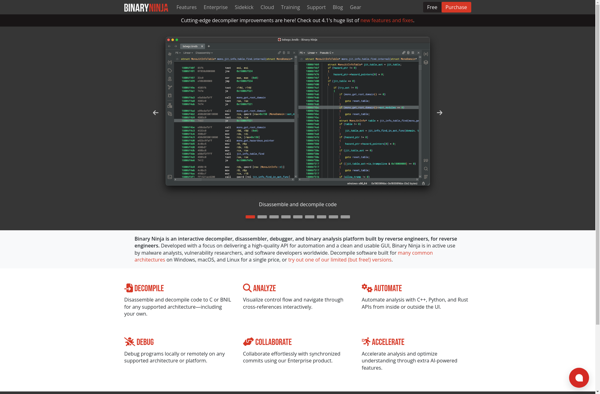
Binary Ninja
Binary Ninja is a versatile reverse engineering platform used for software analysis, vulnerability research, and reverse code engineering. It provides disassembly, decompilation, graphing, scripting, and other functionality to examine and modify binary programs.Some key features of Binary Ninja include:Supports a wide range of architectures including x86, ARM, MIPS, PowerPC, and...
Malcat
Malcat is an open-source malware analysis toolkit designed to help security researchers and incident responders analyze and extract information from malicious files. It provides a modular framework for analyzing different types of files including Portable Executables (PE), MS Office documents, PDF documents, scripts, and memory dumps.Key features of Malcat include:Extracting...
Bokken
Bokken is a graphical user interface intended to be used with pyew and radare2 reverse engineering frameworks. It allows users to disassemble, debug, and analyze malware binaries without needing to have extensive knowledge of command line tools or reverse engineering concepts.Some key features of Bokken include:Intuitive user interface for analyzing...