Token2Shell
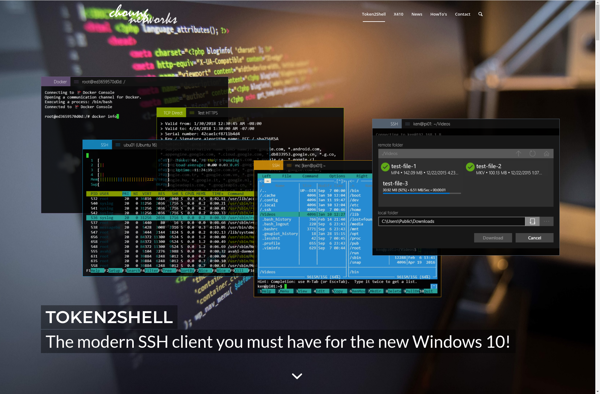
Token2Shell: Penetration Testing Tool
Token2Shell is an open-source tool that allows attackers to escalate privileges and execute code on remote servers by abusing authentication tokens or keys. It can be used for penetration testing with permission.
What is Token2Shell?
Token2Shell is an open-source command line tool written in Golang that generates reverse shells and payload executors by abusing authentication tokens or API keys. It works by using access tokens, API keys, or assumed role keys to invoke AWS API calls for unsigned S3 access. This allows attackers to exploit misconfigurations and improperly scoped permissions to escalate privileges and execute arbitrary code on EC2 instances, Lambda functions, and more.
Token2Shell provides an easy way for penetration testers and security researchers to test for token privilege escalation vulnerabilities in cloud environments. However, it can also be dangerously misused by malicious actors. The tool is intended to reveal flaws in permission scoping and identity management so they can be addressed before exploitation. Proper configuration of AWS permissions and following the principle of least privilege can mitigate the risk of attacks using Token2Shell or similar methods.
In summary, Token2Shell is a powerful open-source tool for testing authorization weaknesses through assumed role and S3 token abuse. White-hat security experts use it to improve cloud security. But it also enables attacks if mishandled, so guidance on ethical usage and responsible disclosure is critical.
Token2Shell Features
Features
- Escalates privileges by abusing authentication tokens
- Executes code on remote servers
- Open source tool for penetration testing
Pricing
- Open Source
Pros
Cons
Official Links
Reviews & Ratings
Login to ReviewThe Best Token2Shell Alternatives
Top Security & Privacy and Penetration Testing and other similar apps like Token2Shell
Here are some alternatives to Token2Shell:
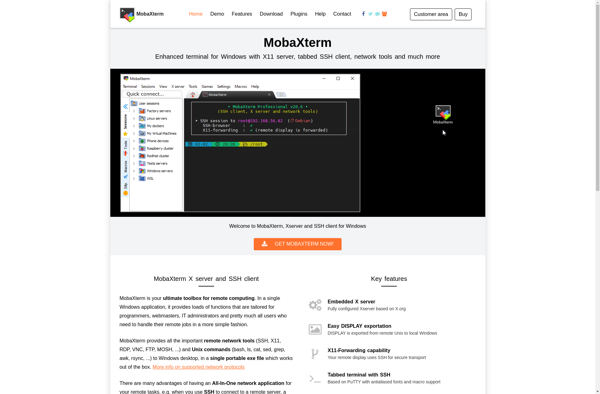
Suggest an alternative ❐MobaXterm
PuTTY

SecureCRT
MTPuTTY (Multi-Tabbed PuTTY)
OpenSSH
Bitvise SSH Client
KiTTY
JuiceSSH