Wazuh
Wazuh is an open source security monitoring solution that provides threat detection, compliance, and data protection. It has capabilities like log analysis, file integrity monitoring, intrusion detection, and more.
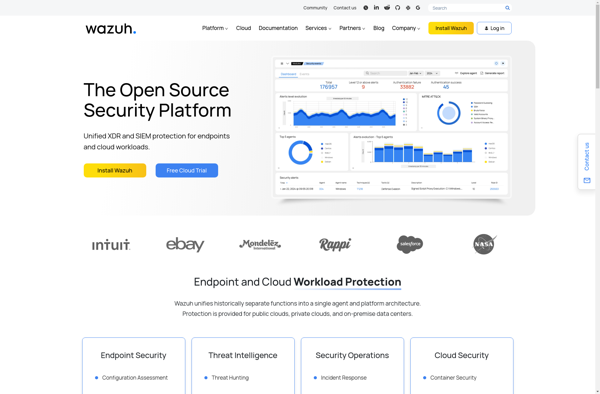
Wazuh: Open Source Security Monitorings
Wazuh provides threat detection, compliance, and data protection with log analysis, file integrity monitoring, intrusion detection capabilities
What is Wazuh?
Wazuh is an open source security monitoring solution built on top of OSSEC. It provides threat detection, compliance, and data protection capabilities. Some of the key features of Wazuh include:
- Log analysis - Analyzes logs from applications, operating systems, and devices to detect suspicious activity, intrusions, policy violations etc.
- File integrity monitoring - Monitors changes to critical files and notifies for unauthorized modifications.
- Intrusion detection - Uses signature and anomaly based detection to identify malware, exploits, and other threats.
- Incident response - Provides alerts and data needed by security teams to respond to incidents.
- Regulatory compliance - Out-of-the-box compliance checks and reporting for regulations like PCI DSS, GDPR, HIPAA.
- Cloud workload protection - Secures and monitors cloud workloads across platforms like AWS, Azure, GCP.
- Centralized management - Manage and monitor security from a single unified console.
Wazuh integrates well with popular tools like Elasticsearch, Logstash, Kibana to provide dashboards, searching, reporting and analytics. It is fully open source and suitable for enterprises, governments and MSSPs.
Wazuh Features
Features
- Log analysis
- File integrity monitoring
- Intrusion detection
- Vulnerability detection
- Configuration assessment
- Incident response
- Regulatory compliance
Pricing
- Open Source
Pros
Open source
Scalable
Customizable rules
Integration with many technologies
Active community support
Cons
Complex installation and configuration
Steep learning curve
Resource intensive for large environments
Limited native Windows support
Official Links
Reviews & Ratings
Login to ReviewThe Best Wazuh Alternatives
Top Security & Privacy and Intrusion Detection & Prevention and other similar apps like Wazuh
Here are some alternatives to Wazuh:
Suggest an alternative ❐Datadog
Datadog is a SaaS-based monitoring and analytics platform for cloud applications. It provides complete visibility into dynamic infrastructures by aggregating metrics, events, and logs from servers, containers, databases, tools, and services. This allows Dev and Ops teams to quickly solve performance problems, prove the root cause of software bugs, spot...
Grafana
Grafana is a feature-rich, open source analytics and monitoring visualization suite. It integrates tightly with a variety of database technologies like Graphite, Prometheus, InfluxDB, Elasticsearch, and more to allow for easy exploration and visualization of time series data. Some key capabilities and benefits of Grafana include:Intuitive graphical UI makes it...
Splunk
Splunk is a software platform that enables users to search, analyze, and visualize the data gathered from the infrastructure, systems, and applications of an organization. It captures, indexes, and correlates real-time data in a searchable repository from which it can generate graphs, reports, alerts, dashboards, and visualizations.Some key features and...
Logstash
Logstash is an open source, server-side data processing pipeline that ingests data from a multitude of sources simultaneously, transforms it, and then sends it to your favorite "stash."It is typically used as part of the ELK stack (Elasticsearch, Logstash, Kibana) for logging use cases. Logstash ingest data from various input...
Graylog
Graylog is an open source log management and analysis platform optimized for high volumes of machine-generated data. It collects, indexes, and analyzes log messages, events, and other time-series data from various systems and applications.Some key features and capabilities of Graylog include:Real-time processing and analysis of log data as it is...
CrowdStrike Falcon
CrowdStrike Falcon is a leading cloud-native endpoint security platform that provides comprehensive protection through next-generation antivirus, endpoint detection and response (EDR), managed threat hunting, IT hygiene, vulnerability management, and threat intelligence services. It leverages artificial intelligence and intuitive security graphs to gain real-time visibility across the entire threat lifecycle and...
Kaspersky Security Cloud Free
Kaspersky Security Cloud Free is a free antivirus software developed by Kaspersky Lab that provides essential protection against a wide range of online threats. It includes the following key features:Real-time malware scanning - Continuously scans files, software, and website traffic for viruses, spyware, ransomware, and other threats.Malicious URL blocking -...
Symantec Endpoint Protection
Symantec Endpoint Protection (SEP) is an antivirus and endpoint security software suite that provides comprehensive protection for devices against malware, viruses, ransomware, and advanced cyber attacks. It is designed to secure endpoints across an organization's network such as desktops, laptops, servers, and mobile devices.Key features of SEP include:Anti-malware and anti-virus...
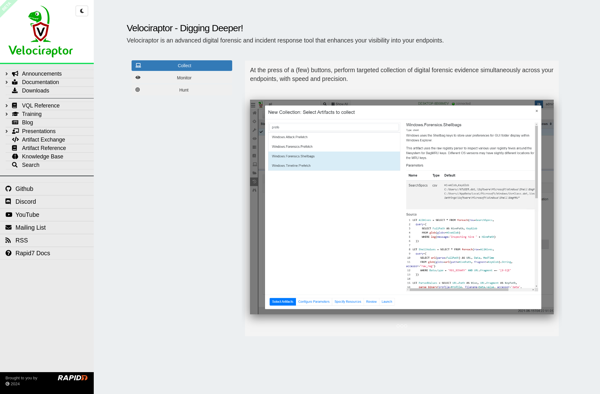
Velociraptor
Velociraptor is an open source endpoint visibility and monitoring tool created by Velocidex. It is designed to provide visibility into endpoints across an organization's network by collecting system information, hunting for indicators of compromise, monitoring for suspicious activity, and enabling incident response.Some key capabilities and features of Velociraptor include:Lightweight agent...
GRR Rapid Response
GRR Rapid Response is an open source incident response framework developed by Google focused on remote live forensics. It is designed to allow security teams to quickly investigate compromises and analyze attacks by enabling remote triage and deep inspection of thousands of systems in an enterprise network.Some key capabilities and...
SIEMonster
SIEMonster is a security information and event management (SIEM) solution tailored for small and medium businesses. It gives organizations greater visibility into their IT infrastructure and applications to detect cyberthreats and data breaches early. Key capabilities include:Real-time collection and correlation of log data from networks, endpoints, cloud services and other...

Ossec
Ossec is an open source host-based intrusion detection system (HIDS) that provides log analysis, file integrity monitoring, policy monitoring, rootkit detection, real-time alerting and active response. It is designed to detect unauthorized intrusions, system anomalies and policy violations on systems. Here are some key features of Ossec:Cross-platform - works on...
