IbVPN
ibVPN is a VPN service provider that offers robust privacy and security features to protect users' data and browsing activities. It has a no-logs policy, allows P2P traffic, and provides AES-256 encryption.
ibVPN: Secure VPN Service for Private Browsing
ibVPN offers robust privacy and security features, including a no-logs policy, P2P traffic support, and AES-256 encryption, making it an ideal choice for users seeking secure browsing experiences.
What is IbVPN?
ibVPN is a virtual private network (VPN) service launched in 2005 that focuses on providing online privacy, security and freedom. It is operated by Ecomaster Solutions based in Romania.
Some key features of ibVPN include:
- Strict no-logs policy to protect users' privacy
- AES 256-bit encryption and support of protocols such as OpenVPN, WireGuard, IKEv2 to keep communications secured
- Servers in over 45 countries around the world to bypass geo-restrictions
- Allows P2P/BitTorrent traffic and works with Netflix
- Supports torrent port forwarding
- Up to 10 simultaneous connections from different devices
- Apps for major platforms like Windows, macOS, iOS, Android and Linux distros
- Accepts anonymous payments via Bitcoin or gift cards
Overall, ibVPN is a good option for those seeking a no-frills secure and private VPN provider that covers the basics well in terms of privacy, security, speeds and streaming capabilities.
IbVPN Features
Features
- AES-256 bit encryption
- No-logs policy
- Kill switch
- Split tunneling
- SOCKS5 web proxy
- Supports P2P traffic
- Apps for all platforms
Pricing
- Subscription-Based
Pros
Robust encryption and privacy features
Large server network
Good speeds
Allows torrenting and P2P
Affordable pricing
Cons
Smaller server network than top VPNs
Fewer protocol choices than competitors
No free trial available
Official Links
Reviews & Ratings
Login to ReviewThe Best IbVPN Alternatives
Top Security & Privacy and Vpn and other similar apps like IbVPN
Here are some alternatives to IbVPN:
Suggest an alternative ❐Psiphon
Psiphon is an open-source internet censorship circumvention tool that was launched in 2007. It allows users to bypass blocked websites and content by routing web traffic through its global server network. Psiphon establishes an encrypted connection between the user's device and one of its international servers, hiding the user's identity...
Proton VPN
Proton VPN is a virtual private network (VPN) service offered by Proton Technologies AG, the company behind ProtonMail encrypted email. Proton VPN aims to provide online privacy, security and freedom by routing internet traffic through an encrypted tunnel to hide users' IP addresses and bypass censorship.Some key features of Proton...
Tor Browser
Tor Browser is a free, open source web browser that allows users to access the internet anonymously and protect their privacy. It is based on Firefox but has been modified to route internet traffic through the Tor network, which encrypts data and bounces communications around a distributed network of relays...

CyberGhost VPN
CyberGhost VPN is a Romania-based virtual private network (VPN) service launched in 2011. It has over 15 million users worldwide and is known for its focus on privacy, security, and user-friendliness.Some key features of CyberGhost VPN include:Intuitive app interface - Easy to use even for beginners with clear labeling and...
Hotspot Shield
Hotspot Shield is a popular virtual private network (VPN) service and app developed by AnchorFree. It provides encrypted connections to protect users' privacy and security when browsing the internet.Some key features of Hotspot Shield include:Encryption of internet traffic to hide IP address and locationAccess to blocked websites and contentWi-Fi security...
NordVPN
NordVPN is a market-leading virtual private network (VPN) service launched in 2012 and based in Panama. It uses advanced encryption to secure users' web traffic and hide their online activities and location. NordVPN has over 5,200 servers in 60 countries worldwide, ensuring reliable connections and allowing users to bypass geo-restrictions.Some...
Mullvad
Mullvad is a Sweden-based VPN service launched in 2009 that emphasizes privacy and anonymity above all else. Unlike many other VPN providers, Mullvad does not require any personal information to create an account. Users can sign up completely anonymously with just a randomly generated account number. In terms of features,...
Freenet
Freenet is an open source, decentralized and censorship-resistant distributed peer-to-peer network designed to provide strong anonymity protections for communication over the internet. It works by pooling the spare bandwidth and storage space of member computers to allow users to anonymously publish websites, share files, and chat on forums without fear...
Windscribe
Windscribe is a virtual private network (VPN) service launched in 2016 that helps protect users' privacy and security while browsing the internet. It works by encrypting data and masking IP addresses to hide online activity and location.Some key features of Windscribe include:Encrypted internet connection to protect against hackers and surveillanceMasks...
Shadowsocks
Shadowsocks is an open-source, cross-platform proxy tool originally created in 2012 by a Chinese developer named clowwindy. It works by creating an encrypted connection between the Shadowsocks client installed on a user's device and a Shadowsocks server installed on a remote server.The encrypted connection helps users bypass firewalls and access...

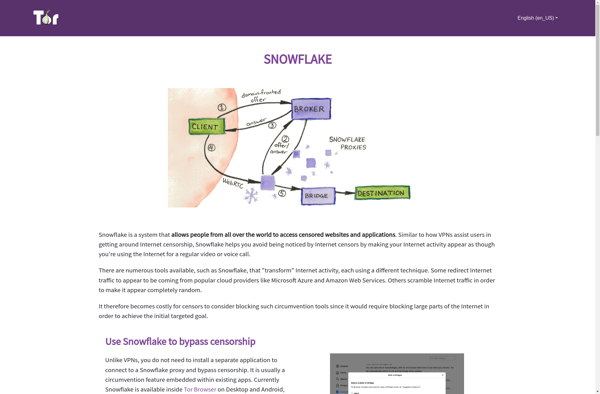
Snowflake Tor
Snowflake Tor is a privacy-focused web browser based on Firefox that routes internet traffic through the Tor network. Tor encrypts traffic and bounces it through a series of relay servers to obscure a user's location and usage from surveillance or network monitoring.By using Tor, Snowflake Tor aims to prevent tracking...