Tcpflow

TcpFlow: Open Source TCP Traffic Flow Capture Tool
Capture and analyze TCP traffic flows using an open source tool that reassembles streams, stores application-layer data with relevant metadata, and works from network interfaces or packet capture files.
What is Tcpflow?
tcpflow is an open source command line tool for capturing TCP traffic flows going through a network. It works by capturing packets from live network interfaces or from packet capture (pcap) files, reassembling TCP streams and sessions, and storing the transmitted application-layer data with relevant TCP metadata like sequence numbers and timestamps.
Some key features of tcpflow include:
- Capturing flows from live interfaces or pcap files
- Reassembly of TCP streams, retaining original payload data
- Output of captured flows to files for later analysis
- Command line options for filtering and post-processing flows
- Handling of TCP retransmissions, out-of-order packets, etc.
- Metadata logging like timestamps, source/destination IPs and ports
tcpflow can be useful for tasks like security analysis, debugging protocol implementations, recovering transferred files from network captures, and gaining visibility into network traffic flows. As it reassembles streams and stores payloads, the output is easier to analyze than raw packet captures.
Since it operates at the TCP layer, tcpflow has relatively low overhead and resource usage compared to analyzing application-layer protocols. Its simple, lightweight implementation makes tcpflow easy to integrate into monitoring and analysis toolchains.
Tcpflow Features
Features
- Captures TCP traffic flows from live network interfaces or packet capture files
- Reassembles TCP streams and stores application-layer data
- Stores TCP metadata like sequence numbers, acknowledgments, window advertisements
- Supports BPF filters for selective capturing
- Outputs flows in various formats like ASCII, CSV, JSON
- Can extract files based on signatures
- Has a library API for programmatic access
Pricing
- Open Source
Pros
Cons
Reviews & Ratings
Login to ReviewThe Best Tcpflow Alternatives
Top Network & Admin and Network Monitoring and other similar apps like Tcpflow
Here are some alternatives to Tcpflow:
Suggest an alternative ❐Wireshark

Netcat
Tcpdump

PsPing
NetworkMiner

Packet Capture
AirSnare

PCAPdroid
Pirni Pro

SmartSniff
Cocoa Packet Analyzer
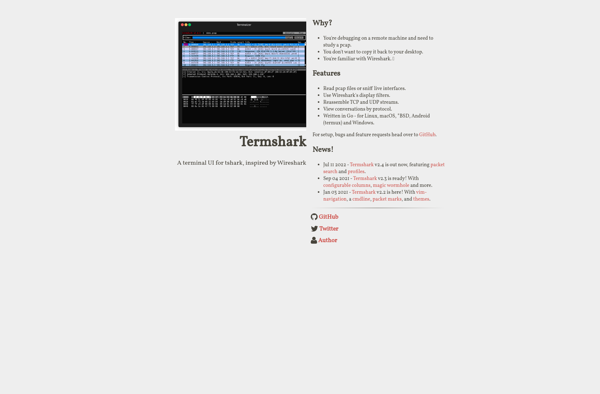
Termshark